Weblogic反序列化漏洞简单补救
Weblogic反序列化在各大论坛的讨论一直是轰轰烈烈的,引发本漏洞其实并不能怪java的反序列化机制,本屌丝曾经也写过几行java代码,并且对weblogic的使用也稍微有点基础。
本文由红客联盟提供。
刚好朋友有个应用使用的是weblogic10.3.6 版本,并且使用WebLogic_EXP.jar 成功执行命令,还好没有被入侵,万幸!!!
测试漏洞存在,应朋友的要求帮忙做个补救,翻遍网上大牛们的技术贴,有两种临时补救的方法,但是尝试过之后对应用有影响,放弃!
今天找到某牛写的贴子,里面提到可以自己禁止JVM 执行系统命令,经过一番研究,写了个servlet 放在系统里面跑了一下,成功防御,直接贴出代码:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 |
import java.io.IOException; import java.io.PrintWriter; import java.security.Permission; import javax.servlet.ServletException; import javax.servlet.http.HttpServlet; import javax.servlet.http.HttpServletRequest; import javax.servlet.http.HttpServletResponse; public class MySecurityServlet extends HttpServlet { /** * Constructor of the object. */ public MySecurityServlet() { super(); } /** * Destruction of the servlet. <br> */ public void destroy() { super.destroy(); // Just puts "destroy" string in log // Put your code here } public void doGet(HttpServletRequest request, HttpServletResponse response) throws ServletException, IOException { this.doPost(request,response); } public void doPost(HttpServletRequest request, HttpServletResponse response) throws ServletException, IOException { response.setContentType("text/html"); PrintWriter out = response.getWriter(); out.println("<!DOCTYPE HTML PUBLIC \"-//W3C//DTD HTML 4.01 Transitional//EN\">"); out.println("<HTML>"); out.println(" <HEAD><TITLE>Errot</TITLE></HEAD>"); out.println(" <BODY>"); out.println("Security denied!!!"); out.println(" </BODY>"); out.println("</HTML>"); out.flush(); out.close(); } /** * Initialization of the servlet. <br> * @throws ServletException if an error occurs */ public void init() throws ServletException { SecurityManager originalSecurityManager = System.getSecurityManager(); if (originalSecurityManager == null) { // 创建自己的SecurityManager SecurityManager sm = new SecurityManager() { private void check(Permission perm) { // 禁止exec if (perm instanceof java.io.FilePermission) { String actions = perm.getActions(); if (actions != null && actions.contains("execute")) { System.out.println("警告:>>检测到 weblogic 反序列化攻击..."); throw new SecurityException("execute denied!"); } } // 禁止设置新的SecurityManager,保护自己 if (perm instanceof java.lang.RuntimePermission) { String name = perm.getName(); if (name != null && name.contains("setSecurityManager")) { System.out.println("警告:<<检测到 weblogic 反序列化攻击..."); throw new SecurityException("System.setSecurityManager denied!"); } } } public void checkPermission(Permission perm) { check(perm); } public void checkPermission(Permission perm, Object context) { check(perm); } }; System.setSecurityManager(sm); } } } web.xml 配置文件中添加如下内容: <servlet> <servlet-name>MySecurityServlet</servlet-name> <servlet-class>MySecurityServlet</servlet-class> <load-on-startup>0</load-on-startup> </servlet> <servlet-mapping> <servlet-name>MySecurityServlet</servlet-name> <url-pattern>/servlet/MySecurityServlet</url-pattern> </servlet-mapping> |
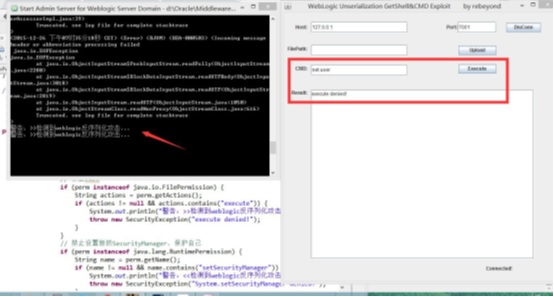
下面是本地测试的结果
如果您需要了解更多内容,可以
加入QQ群:486207500
直接询问:010-68438880-8669